156-215.77 Exam Dumps - Check Point Certified Security Administrator
Which of the following methods will provide the most complete backup of an R77 configuration?
Static NAT connections, by default, translate on which firewall kernel inspection point?
Which Check Point address translation method allows an administrator to use fewer ISP-assigned IP addresses than the number of internal hosts requiring Internet connectivity?
You are MegaCorp’s Security Administrator. There are various network objects which must be NATed. Some of them use the Automatic Hide NAT method, while others use the Automatic Static NAT method. What is the rule order if both methods are used together? Give the BEST answer.
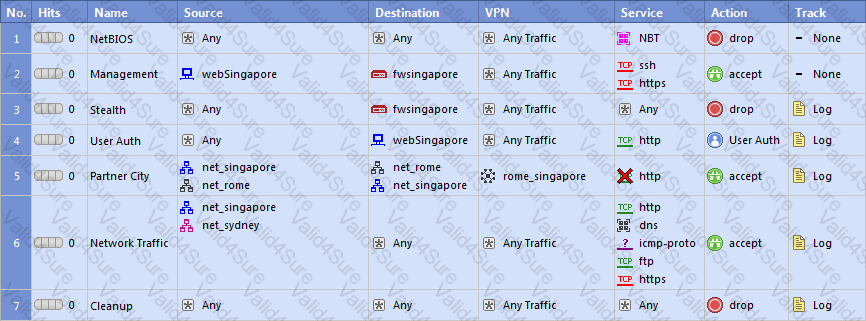
Several Security Policies can be used for different installation targets. The Firewall protecting Human Resources’ servers should have its own Policy Package. These rules must be installed on this machine and not on the Internet Firewall.
How can this be accomplished?
You are working with three other Security Administrators.
Which SmartConsole component can be used to monitor changes to rules or object properties made by the other administrators?