156-215.81 Exam Dumps - Check Point Certified Security Administrator R81.20 CCSA (156-215.81.20)
Question # 98
Identity Awareness allows easy configuration for network access and auditing based on what three items?
Question # 99
Fill in the blank: Each cluster, at a minimum, should have at least ___________ interfaces.
Question # 100
Consider the Global Properties following settings:
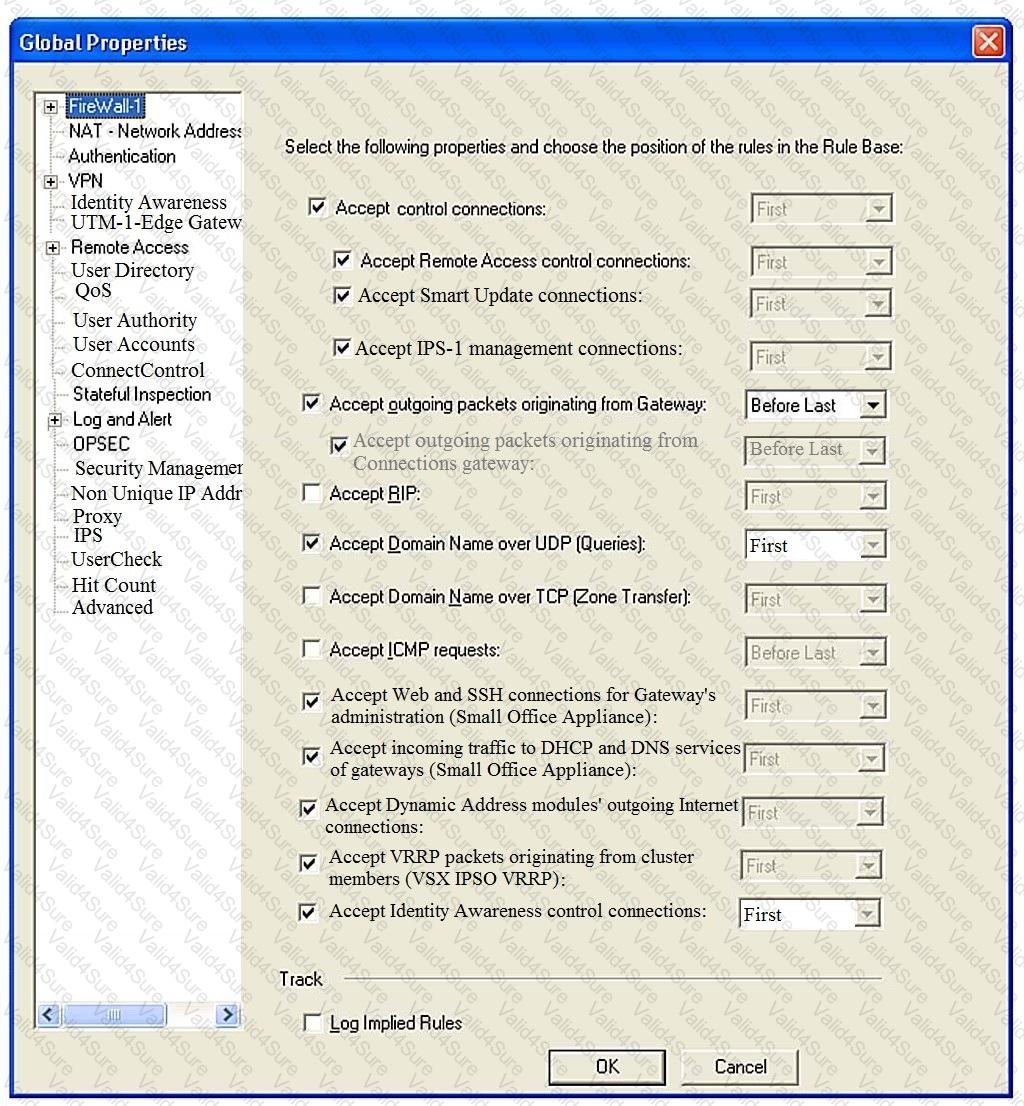
The selected option “Accept Domain Name over UDP (Queries)†means:
Question # 101
You have discovered suspicious activity in your network. What is the BEST immediate action to take?
Question # 103
Which information is included in the “Extended Log†tracking option, but is not included in the “Log†tracking option?
Question # 104
Session unique identifiers are passed to the web api using which http header option?