1Y0-403 Exam Dumps - Citrix Virtual Apps and Desktops 7 Assessment Design and Advanced Configurations
Scenario: A Citrix Consultant is designing a new Citrix Virtual Desktops environment. During the user segmentation process, a Citrx Architect collected a small amount of data about user requirements, but was NOT able to create well-defined user groups.
Which user-segmentation actions should the consultant pursue?
Scenario: A Citrix Architect is designing a new Citrix Virtual Apps and Desktops environment. Management has advised that they have a limited budget for the new solution. However, they still expect the design to account for future growth without the need to redesign or repurchase central hardware components. Additionally, the current 1 Gb network infrastructure CANNOT be replaced within the scope of this project. The architect has determined that the company can support both current and future load with 2 to 3 separate Virtual Delivery Agent (VDA) machine images.
Which two features should the architect consider while designing the Citrix Hypervisors for the proposed Citrix environment? (Choose two.)
Scenario: A Citrix Architect is designing a new Citrix Virtual Apps and Desktops environment. The architect's objective is to create a configuration to automatically reroute network traffic to the second NIC within the bond. The goal is to avoid a loss of productivity should the primary Citrix Hypervisor host NIC fail. Each hypervisor currently consists of a single, active 10 GB NIC and a second, dormant 1 GB NIC.
Which two network interface configurations should the architect implement? (Choose two.)
Scenario: A Citrix Architect is designing a new Citrix Virtual Apps and Desktops environment. The architect has identified the requirements, based on the assessment and early stages of the design.
Click the Exhibit button to view the requirements.
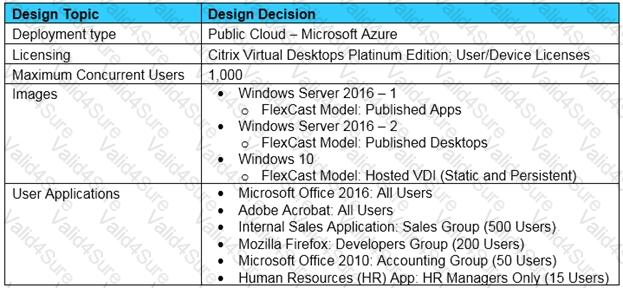
Additionally, the IT team identified 2 provisioning strategy requirements:
- Should be compatible with planned design decisions
- Should minimize required time to perform image and application updates
Which provisioning method should the architect use for the environment, based on the design decisions and requirements shown in the exhibit?
Scenario: A Citrix Architect is designing a new Citrix Virtual Apps and Desktops environment. The environment consists of 4 Citrix Hypervisor hosts, each running 10 virtual machines (VMs). To meet company security standards for the environment, the IT team will need to perform routine VM snapshots, data backups, and threat scans.
Which two matters should the architect consider when securing a backup plan for the company? (Choose two.)