1z0-908 Exam Dumps - MySQL 8.0 Database Administrator
Question # 4
Your my.cnf file contains these settings:
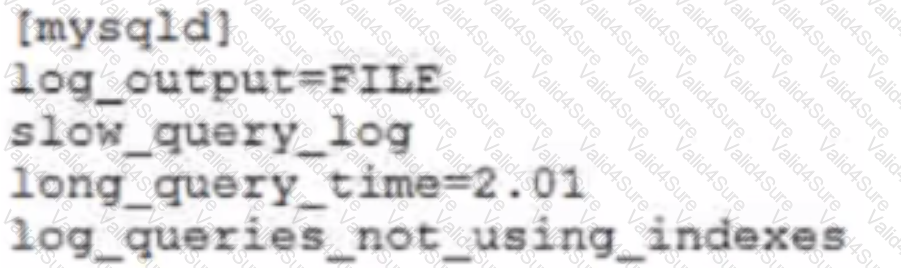
You want to log queries that looked at a minimum of 5000 records and either took longer than 5 seconds to run or did not use indexes.
Which contains all the settings that you need to add to or modify the slow log configuration?
Question # 5
Which four are types of information stored in the MySQL data dictionary? (Choose four.)
Question # 6
Examine this command, which executes successfully on InnoDB Cluster: dba.dropMetadataSchema()
Which two statements are true? (Choose two.)
Question # 7
Which two are valid uses for binary logs on a MySQL instance? (Choose two.)