200-301 Exam Dumps - Cisco Certified Network Associate
Which alternative to password authentication Is Implemented to allow enterprise devices to log in to the corporate network?
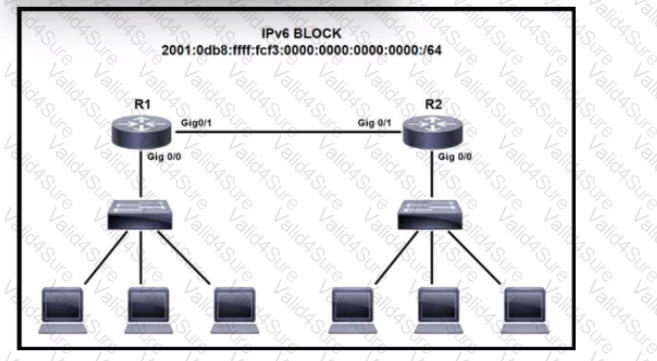
Refer to the exhibit. IPv6 is being Implemented within the enterprise. The command Ipv6 unlcast-routing is configure. Interlace GlgO/0 on R1 must be configured to provide a dynamic assignment using the assigned IPv6 block Which command accomplishes this task?
Refer to the exhibit.
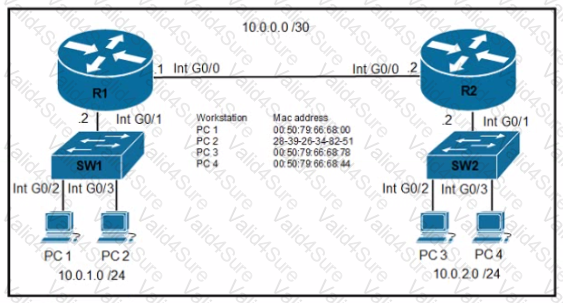
An engineer must configure the interface that connects to PC 1 and secure it in a way that only PC1 is allowed to use the port No VLAN tagging can be used except for a voice VLAN. Which command sequence must be entered to configure the switch?
A)

B)

C)
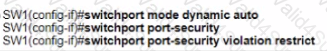
D)

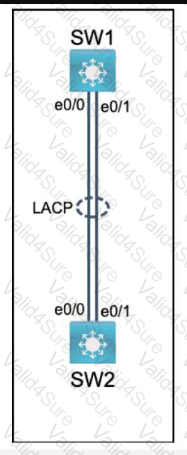
Physical connectivity is implemented between the two Layer 2 switches,
and the network connectivity between them must be configured.
I . Configure an LACP EtherChanneI and number it as 44; configure it
between switches SWI and SW2 using interfaces EthernetO/O and
Ethernet0/1 on both sides. The LACP mode must match on both ends.
2. Configure the EtherChanneI as a trunk link.
3. Configure the trunk link with 802. Iq tags.
4. Configure VLAN 'MONITORING' as the untagged VLAN of the
EtherChannel.
==================
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
Refer to the exhibit.
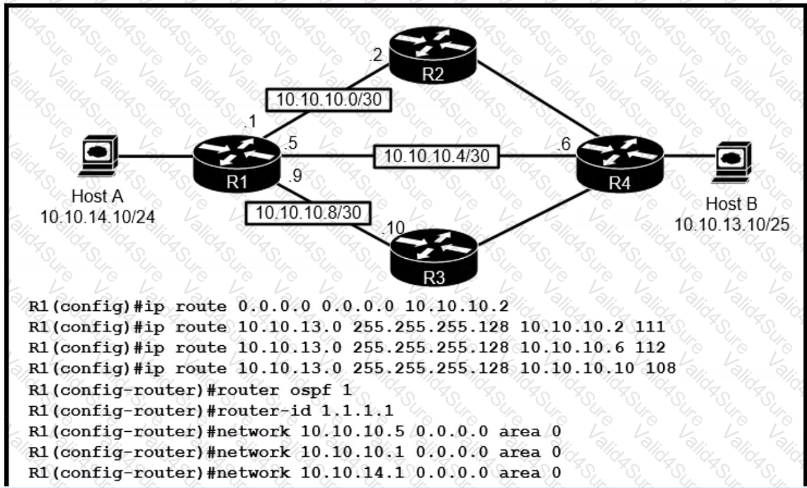
R1 has just received a packet from host A that is destined to host B. Which route in the routing table is used by R1 to reac B?
A WLC sends alarms about a rogue AP, and the network administrator verifies that the alarms are caused by a legitimate autonomous AP.