212-82 Exam Dumps - Certified Cybersecurity Technician (CCT)
Tristan, a professional penetration tester, was recruited by an organization to test its network infrastructure. The organization wanted to understand its current security posture and its strength in defending against external threats. For this purpose, the organization did not provide any information about their IT infrastructure to Tristan. Thus, Tristan initiated zero-knowledge attacks, with no information or assistance from the organization.
Which of the following types of penetration testing has Tristan initiated in the above scenario?
You are working as a Security Consultant for a top firm named Beta Inc.
Being a Security Consultant, you are called in to assess your company's situation after a ransomware attack that encrypts critical data on Beta Inc. servers. What is the MOST critical action you have to take immediately after identifying the attack?
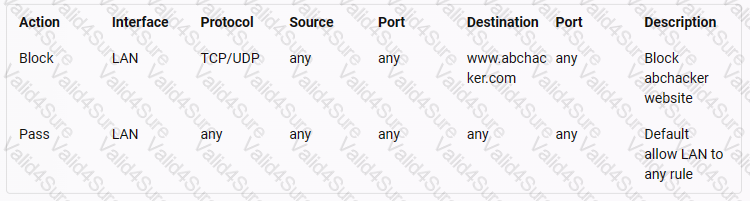
A pfSense firewall has been configured to block a web application www.abchacker.com. Perform an analysis on the rules set by the admin and select the protocol which has been used to apply the rule.
Hint: Firewall login credentials are given below:
Username: admin
Password: admin@l23
Myles, a security professional at an organization, provided laptops for all the employees to carry out the business processes from remote locations. While installing necessary applications required for the business, Myles has also installed antivirus software on each laptop following the company's policy to detect and protect the machines from external malicious events over the Internet.
Identify the PCI-DSS requirement followed by Myles in the above scenario.
Hotel Grande offers luxury accommodations and emphasizes top-notch service for its guests. One such service is secure, high-speed Wi-FI access In every room. The hotel wishes to deploy an authentication method that would give individual guests a seamless experience without compromising security. This method should ideally provide a balance between convenience and strong security. Which of the following should Hotel Grande use?
Alpha Finance, a leading banking institution, is launching anew mobile banking app. Given the sensitive financial data involved, it wants to ensure that Its application follows the best security practices. As the primary recommendation, which guideline should Alpha Finance prioritize?
As a cybersecurity technician, you were assigned to analyze the file system of a Linux image captured from a device that has been attacked recently. Study the forensic image'Evidenced.img" in the Documents folder of the "Attacker Machine-1" and identify a user from the image file. (Practical Question)
Richards, a security specialist at an organization, was monitoring an IDS system. While monitoring, he suddenly received an alert of an ongoing intrusion attempt on the organization's network. He immediately averted the malicious actions by implementing the necessary measures.
Identify the type of alert generated by the IDS system in the above scenario.