300-415 Exam Dumps - Implementing Cisco SD-WAN Solutions (300-415 ENSDWI)
Which component is used for stateful inspection of TCP, UDP. and ICMP flows in Cisco SD-WAN firewall policies?
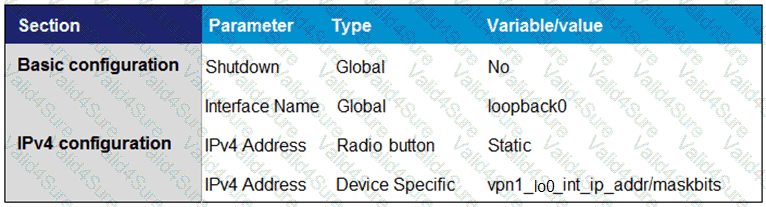
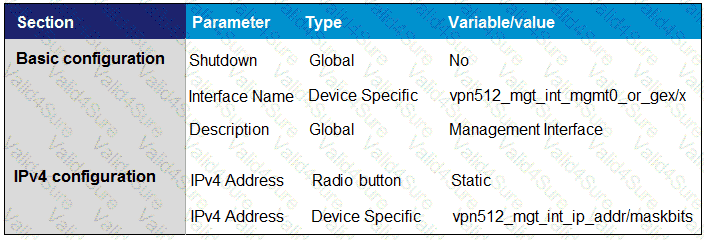
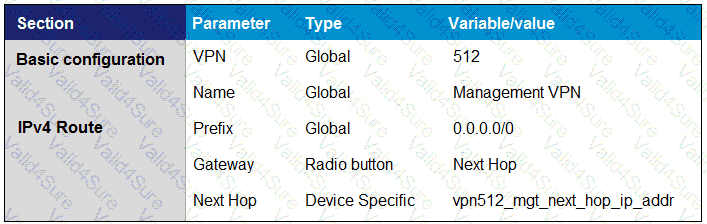
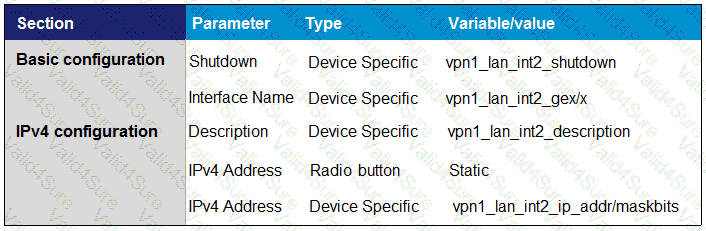
Drag and drop the definitions from the left to the configuration on the right.

Which two prerequisites must be met before the Cloud onRamp for laaS is initiated on vManage to expand to the AWS cloud? (Choose two)
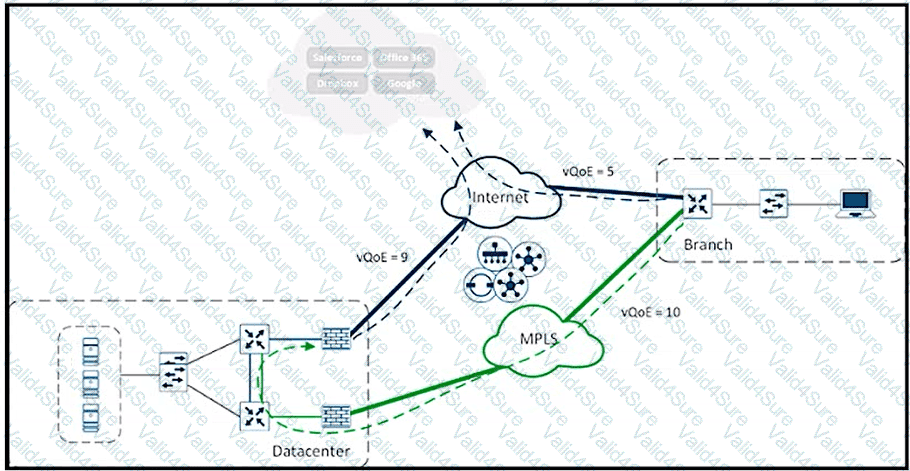
Refer to the exhibit. A user in the branch is connecting to Office 365 for the first time. Over which path does the branch WAN Edge router traffic follow?
Which SD-WAN component is configured to enforce a policy to redirect branch-to-branch traffic toward a network service such as a firewall or IPS?
Which two services are critical for zero touch provisioning on-boarding? (Choose two)
Refer to the exhibit.
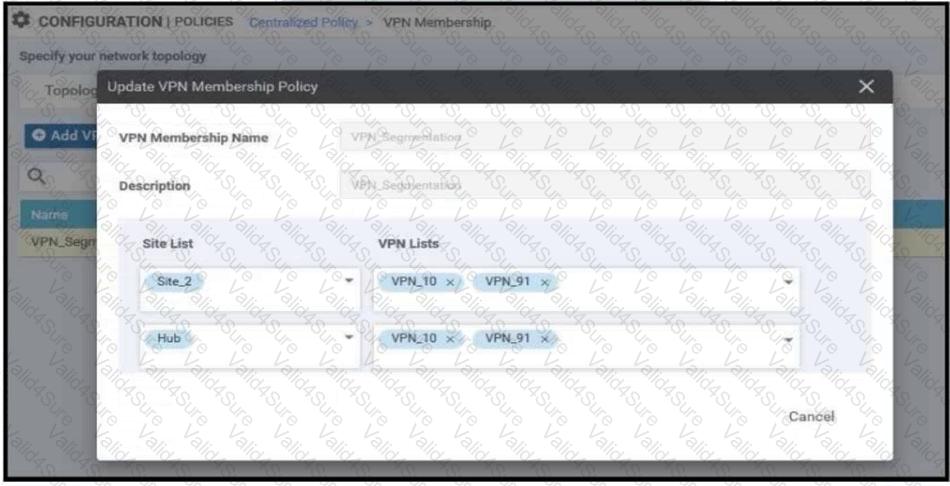
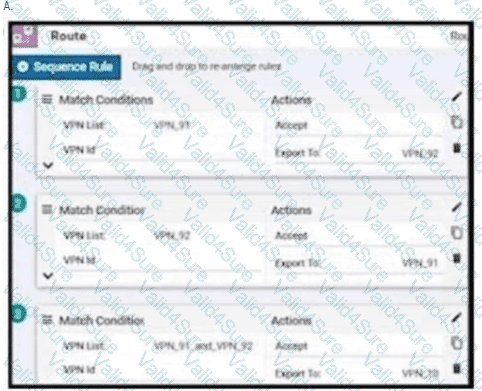
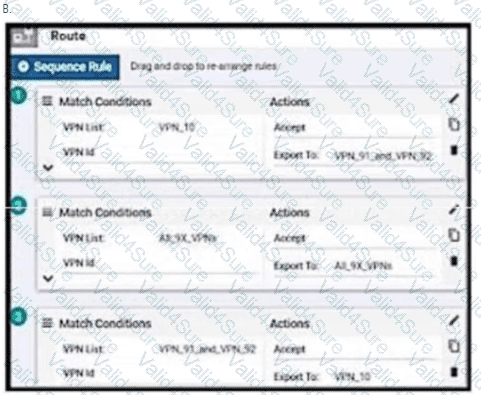
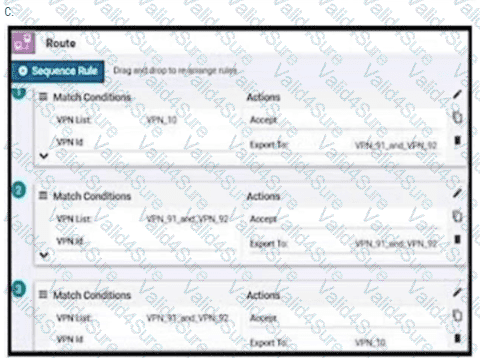
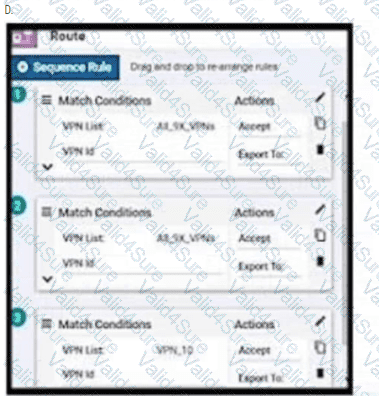
An enterprise has hub and spoke topology where it has several VPNs. An engineer must allow users in VPN91 to reach users in VPN92 and VPN10 to reach VPN91 and VPN92. Which configuration meets these requirements?