312-76 Exam Dumps - EC-Council Disaster Recovery Professional v3 (EDRP)
Searching for workable clues to ace the ECCouncil 312-76 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 312-76 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which of the following terms refers to a holistic management process that identifies potential threats to an organization and its impacts on business operations? It further provides a framework for building organizational resilience with the capability for an effective response that safeguards the interests of its key stakeholders, reputation, brand, and value-creating activities?
Katie was setting up disaster recovery teams in her organization to combat any disaster that occurred. One of the most important teams was the disaster recovery coordinator. Having two names in mind for the post, Katie interviewed the two people for the roles and responsibilities of the disaster recovery coordinator. Which of the following statements should either of the interviewees use to get the post?
Gloria was auditing the BCP prepared by one of her clients. The BCP audit stage that she was currently examining ascertained whether operational resiliency and continuity was being encouraged, and if the BCP was overfunded or underfunded. Which BCP audit stage was Gloria examining?
Which of the following terms measures the severity of the impact of a risk on a business?
Which of the following terms refers to the act, manner, or practice of an organization to bring systems, applications, and data back to "normal" conditions in a prescribed and acceptable time frame?
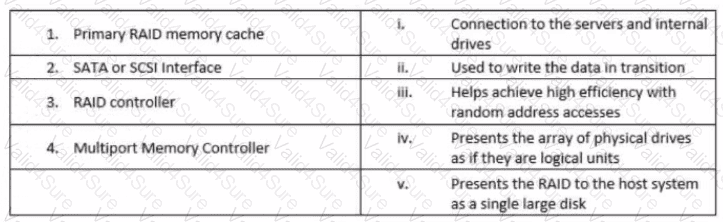
Which of the following terms refers to a high-speed data transmission technique that provides access to consolidated block-level storage?
After learning about the features of PASIS architecture, James decides to implement the same in his startup. After a few months, an earthquake destroyed a few storage nodes in the central server rendering the data in those nodes unreadable. Since James had implemented the PASIS architecture, he was able to recover the data present in the destroyed nodes. Which feature of PASIS architecture allowed James to recover the data?