400-007 Exam Dumps - Cisco Certified Design Expert (CCDE v3.1)
Refer to the diagram.
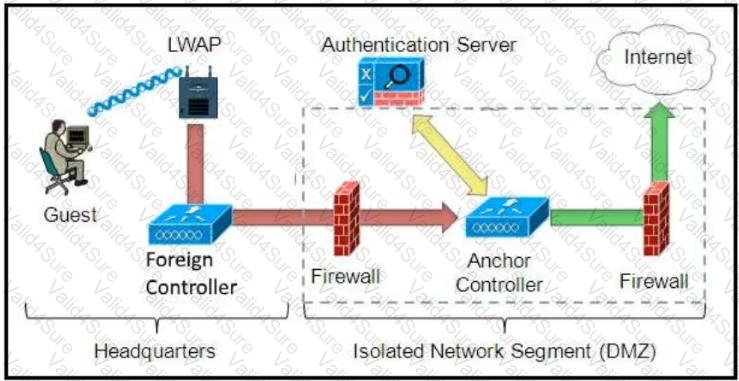
Which solution must be used to send traffic from the foreign wireless LAN controller to the anchor wireless LAN controller?
How must the queue sizes be designed to ensure that an application functions correctly?
Which development model is closely associated with traditional project management?
Which two factors must be considered for high availability in campus LAN designs to mitigate concerns about unavailability of network resources? (Choose two.)
Which function is performed at the access layer of the three-layer hierarchical network design model?
You have been asked to design a remote access VPN solution to support up to 2000 devices. You must ensure that only corporate assets are allowed to connect to the VPN, and users must authenticate to gain access of their based on their user role. Users must use a password that they are already using to access existing applications . A user may not always use the same device to access the VPN. Which two options combined meet the requirements? (Choose two)
Which two statements describe the hierarchical LAN design model? (Choose two)