CAS-004 Exam Dumps - CompTIA SecurityX Certification Exam
Searching for workable clues to ace the CompTIA CAS-004 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s CAS-004 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
An organization is working to secure its development process to ensure developers cannot deploy artifacts directly into the production environment. Which of the following security practice recommendations would be the best to accomplish this objective?
After establishing coding standards and integrating software assurance tools into CI/CD pipelines, an architect continues to find too many different coding styles throughout the team. Which of the following additional measures can the architect take to help improve consistency?
An multinational organization was hacked, and the incident response team's timely action prevented a major disaster Following the event, the team created an after action report. Which of the following is the primary goal of an after action review?
A user logged in to a web application. Later, a SOC analyst noticed the user logged in to systems after normal business hours. The end user confirms the log-ins after hours were unauthorized. Following an investigation, the SOC analyst determined that the web server was running an outdated version of OpenSSL. No other suspicious user log-ins were found. Which of the following describes what happened and how to fix it?
A major broadcasting company that requires continuous availability to streaming content needs to be resilient against DDoS attacks Which of the following is the MOST important infrastructure security design element to prevent an outage7
A technology company developed an in-house chat application that is used only by developers. An open-source library within the application has been deprecated. The facts below are provided:
The cost of replacing this system is nominal.
The system provides no revenue to the business.
The system is not a critical part of the business.
Which of the following is the best risk mitigation strategy?
A SOC analyst received an alert about a potential compromise and is reviewing the following SIEM logs:
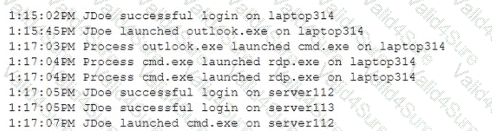
Which of the following is the most appropriate action for the SOC analyst to recommend?
The results of an internal audit indicate several employees reused passwords that were previously included in a published list of compromised passwords. The company has the following employee password policy:
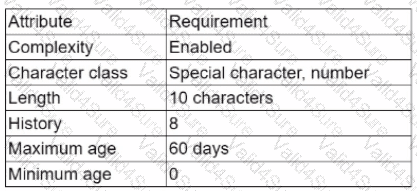
Which of the following should be implemented to best address the password reuse issue? (Select two).