CS0-003 Exam Dumps - CompTIA CyberSecurity Analyst CySA+ Certification Exam
A security analyst is reviewing the following alert that was triggered by FIM on a critical system:
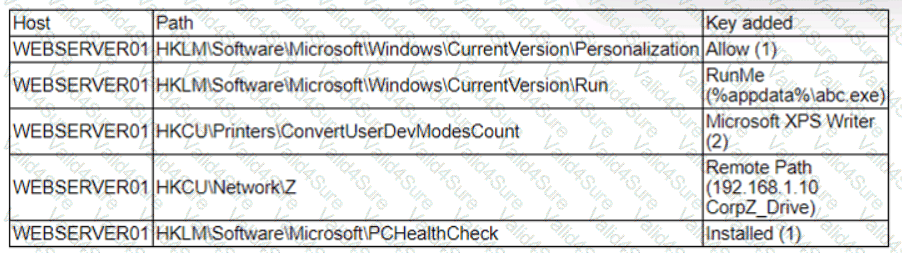
Which of the following best describes the suspicious activity that is occurring?
A penetration tester submitted data to a form in a web application, which enabled the penetration tester to retrieve user credentials. Which of the following should be recommended for remediation of this application vulnerability?
A security audit for unsecured network services was conducted, and the following output was generated:
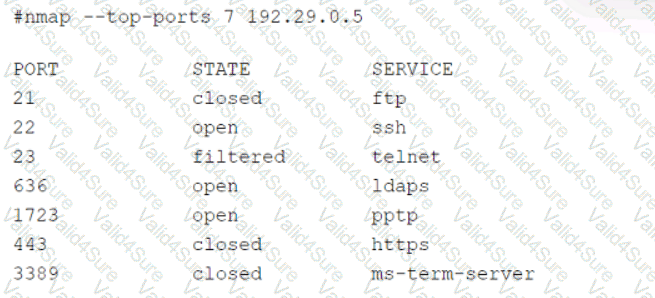
Which of the following services should the security team investigate further? (Select two).
A recent penetration test discovered that several employees were enticed to assist attackers by visiting specific websites and running downloaded files when prompted by phone calls. Which of the following would best address this issue?
A security manager reviews the permissions for the approved users of a shared folder and finds accounts that are not on the approved access list. While investigating an incident, a user discovers data discrepancies in the file. Which of the following best describes this activity?
A user downloads software that contains malware onto a computer that eventually infects numerous other systems. Which of the following has the user become?
The security team at a company, which was a recent target of ransomware, compiled a list of hosts that were identified as impacted and in scope for this incident. Based on the following host list:
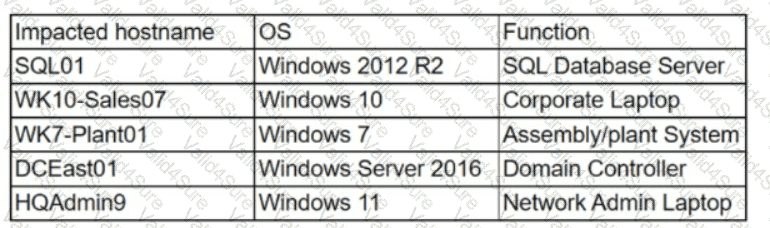
Which of the following systems was most pivotal to the threat actor in its distribution of the encryption binary via Group Policy?
An analyst reviews a recent government alert on new zero-day threats and finds the following CVE metrics for the most critical of the vulnerabilities:
CVSS: 3.1/AV:N/AC: L/PR:N/UI:N/S:C/C:H/I:H/A:H/E:U/RL:W/RC:R
Which of the following represents the exploit code maturity of this critical vulnerability?