H12-222 Exam Dumps - Huawei Certified Network Professional-R&S-IENP
Which of the following statements regarding Free Mobility of the Agile Controller are true? (Multiple Choice)
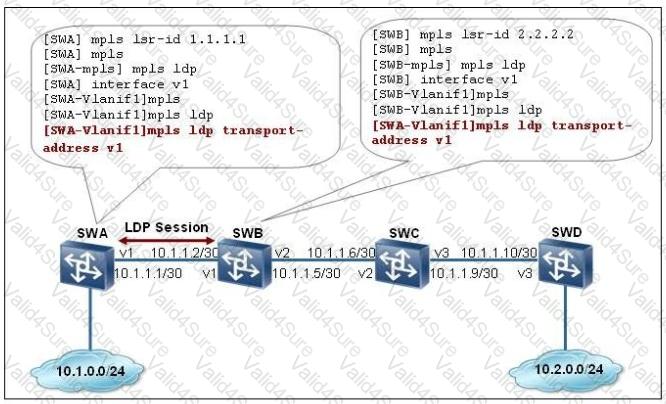
On the MPLS network shown in the following figure, which of the following statements are true? (Multiple Choice)
Which remote alarm notification modes are supported by eSight? (Multiple Choice)
Which of the following statements regarding the free mobility application scenario of the Agile Controller is false?
DHCP snooping is a security feature. Which of the following statements regarding DHCP snooping is false?
Application Specific Packet Filter (ASPF) is packet filtering based on the application layer. ASPF checks application layer protocol information, monitors the application layer protocol status of connections, and uses the Servermap table to achieve a special security mechanism. Which of the following statements regarding ASPF and Servermap is false?