Note! Following H12-711_V3.0 Exam is Retired now. Please select the alternative replacement for your Exam Certification.
The new exam code is H12-711_V4.0
H12-711_V3.0 Exam Dumps - HCIA-Security V3.0
Question # 67
In practical applications, asymmetric encryption is mainly used to encrypt user data
Question # 68
In which of the following scenarios does the firewall generate the Server map table? ( )
Question # 70
in the administratorUSGWhich of the following operations are required during the firewall software version upgrade? (multiple choice)
Question # 71
Please order the following project implementation steps from project initiation.[fill in the blank]*
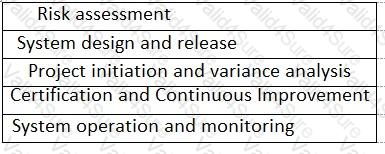
Question # 72
UDPA port scan is when an attacker sends a zero byte lengthUDPmessage to a specific port of the target host, if the port is open, it will return aICMPPort reachable data packets.