Note! Following JN0-334 Exam is Retired now. Please select the alternative replacement for your Exam Certification.
The new exam code is JN0-335
JN0-334 Exam Dumps - Security-Specialist (JNCIS-SEC)
Question # 4
Click the Exhibit button.
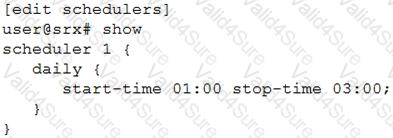
You have configured the scheduler shown in the exhibit to prevent users from accessing certain websites from 1:00 PM to 3:00 PM Monday through Friday. This policy will remain in place until further notice. When testing the policy, you determine that the websites are still accessible during the restricted times.
In this scenario, which two actions should you perform to solve the problem? (Choose two.)
Question # 5
Click the Exhibit button.
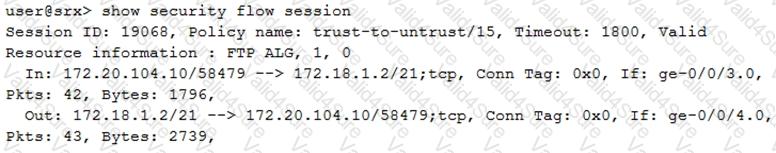
Which two statements are true about the session shown in the exhibit? (Choose two.)
Question # 6
Click the Exhibit button.
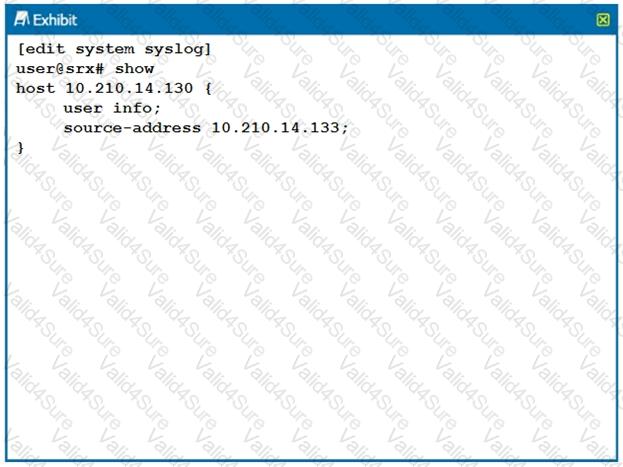
Referring to the configuration shown in the exhibit, which two statements are true? (Choose two.)
Question # 8
How many nodes are configurable in a chassis cluster using SRX Series devices?