NS0-527 Exam Dumps - NetApp Certified Implementation Engineer - Data Protection
A customer wants to assign a user to a build-in SnapCenter RBAC Role that will allow them to review and start existing SnapMirror processes only.
In this scenario, which Role will allow the customer to accomplish this task?
Your DevOps team reported that one virtual machine on a VMware datastore has been corrupted due to a ransomware attack.
In this scenario, which two methods would solvethe issue? (Choose two.)
You have deployed a 4-node fabric MetroCluster configuration for cross-site disaster-recovery protection. In this scenario, which two statements are correct for an automatic unplanned switchover (AUSO) operation?
(Choose two.)
You have two ONTAP clusters, cluster1 and cluster2. Cluster1 has an SVM serving SMB3 data and you want to protect it by replicating it to cluster2 using SVM DR. The source and destination subnets are identical. You want to retain the CIFS server security of the SVM at the destination site.
In this scenario, which three steps would you take to configure the SVM DR relationship? (Choose three.)
You are using Veeam Backup & Replication to create Snapshot-based backups of your VMware environment running ONTAP. You added your primary and secondary ONTAP cluster to the Veeam Storage inventory.
However, you are unable to select your secondary ONTAP cluster as a secondary target for your Veeam backup job.
In ONTAP System Manager, which action solves this problem?
Click the Exhibit button.
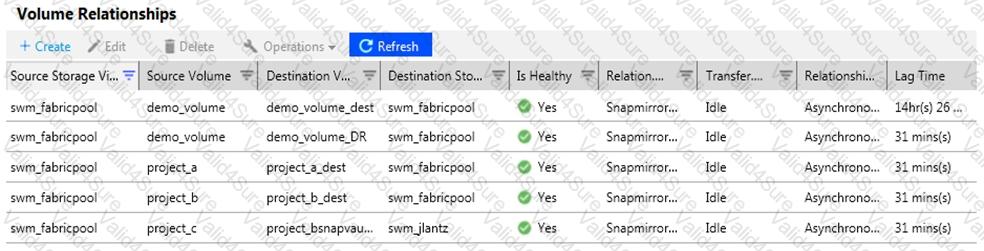
A customer wants to ensure that their volumes are protected. In ONTAP System Manager, under the Protectionsection, you see the screen that is shown in the exhibit. The company has an asynchronous mirror policy of less than a 60-minute lag.
Referring to the exhibit, which volume has a lag that exceeds the company policy?