NSE4_FGT-6.2 Exam Dumps - Fortinet NSE 4 - FortiOS 6.2
An administrator needs to strengthen the security for SSL VPN access. Which of the following statements are best practices to do so? (Choose three.)
View the exhibit.
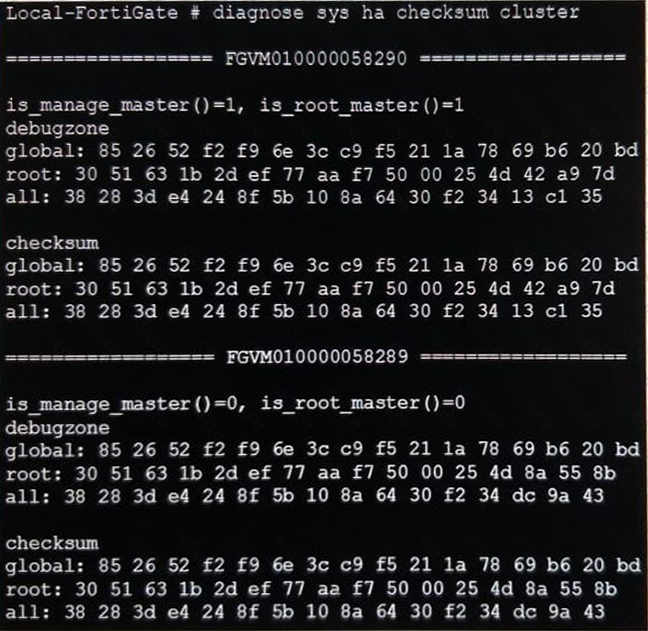
Based on this output, which statements are correct? (Choose two.)
View the exhibit. Which of the following statements is true regarding the configuration settings?
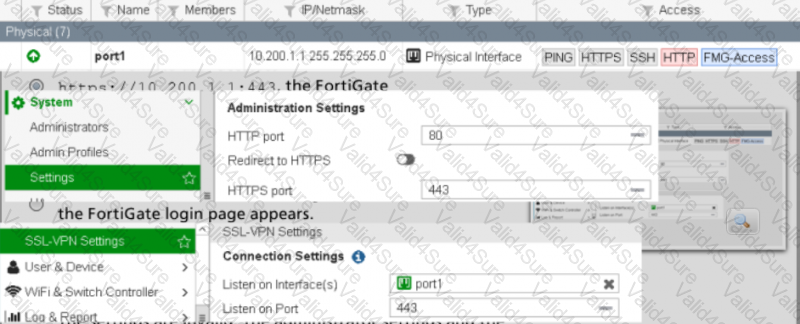
Response:
An administrator wants to create a policy-based IPsec VPN tunnel betweeb two FortiGate devices. Which configuration steps must be performed on both devices to support this scenario? (Choose three.)
Why must you use aggressive mode when a local FortiGate IPSec gateway hosts multiple dialup tunnels?
What criteria does FortiGate use to look for a matching firewall policy to process traffic? (Choose two.)
What is the limitation of using a URL list and application control on the same firewall policy, in NGFW policy-based mode?
Which of the following statements about central NAT are true? (Choose two.)