PT0-001 Exam Dumps - CompTIA PenTest+ Exam
The results of a basic compliance scan show a subset of assets on a network. This data differs from what is shown on the network architecture diagram, which was supplied at the beginning of the test. Which of the following are the MOST likely causes for this difference? (Select TWO)
Which of the following can be used to perform online password attacks against RDP?
A company planned for and secured the budget to hire a consultant to perform a web application penetration test. Upon discovered vulnerabilities, the company asked the consultant to perform the following tasks:
• Code review
• Updates to firewall setting
Given the following Python script:
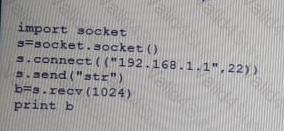
Which of the following actions will it perform?
A senior employee received a suspicious email from another executive requesting an urgent wire transfer.
Which of the following types of attacks is likely occurring?
Defining exactly what is to be tested and the results to be generated from the test will help prevent?
While engaging clients for a penetration test from highly regulated industries, which of the following is usually the MOST important to the clients from a business perspective?
A penetration tester is required to perform OSINT on staff at a target company after completing the infrastructure aspect. Which of the following would be the BEST step for the penetration tester to take?