PT0-003 Exam Dumps - CompTIA PenTest+ Exam
Searching for workable clues to ace the CompTIA PT0-003 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s PT0-003 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
During a penetration test, the tester gains full access to the application's source code. The application repository includes thousands of code files. Given that the assessment timeline is very short, which of the following approaches would allow the tester to identify hard-coded credentials most effectively?
During a security assessment, a penetration tester gains access to an internal server and manipulates some data to hide its presence. Which of the following is the best way for the penetration tester to hide the activities performed?
A penetration tester needs to complete cleanup activities from the testing lead. Which of the following should the tester do to validate that reverse shell payloads are no longer running?
A penetration tester needs to evaluate the order in which the next systems will be selected for testing. Given the following output:
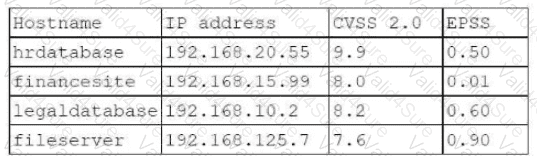
Which of the following targets should the tester select next?
Which of the following authorizations is mandatory when a penetration tester is involved in a complex IT infrastructure?
Which of the following is the most efficient way to exfiltrate a file containing data that could be sensitive?
Which of the following tasks would ensure the key outputs from a penetration test are not lost as part of the cleanup and restoration activities?
A penetration tester is researching a path to escalate privileges. While enumerating current user privileges, the tester observes the following:
SeAssignPrimaryTokenPrivilege Disabled
SeIncreaseQuotaPrivilege Disabled
SeChangeNotifyPrivilege Enabled
SeManageVolumePrivilege Enabled
SeImpersonatePrivilege Enabled
SeCreateGlobalPrivilege Enabled
SeIncreaseWorkingSetPrivilege Disabled
Which of the following privileges should the tester use to achieve the goal?