SC-100 Exam Dumps - Microsoft Cybersecurity Architect
Searching for workable clues to ace the Microsoft SC-100 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s SC-100 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
You need to recommend a solution to scan the application code. The solution must meet the application development requirements. What should you include in the recommendation?
You need to recommend a solution to resolve the virtual machine issue. What should you include in the recommendation? (Choose Two)
You need to recommend a solution to meet the security requirements for the InfraSec group.
What should you use to delegate the access?
You need to recommend a solution to secure the MedicalHistory data in the ClaimsDetail table. The solution must meet the Contoso developer requirements.
What should you include in the recommendation?
Your on-premises network contains an e-commerce web app that was developed in Angular and Nodejs. The web app uses a MongoDB database. You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone.
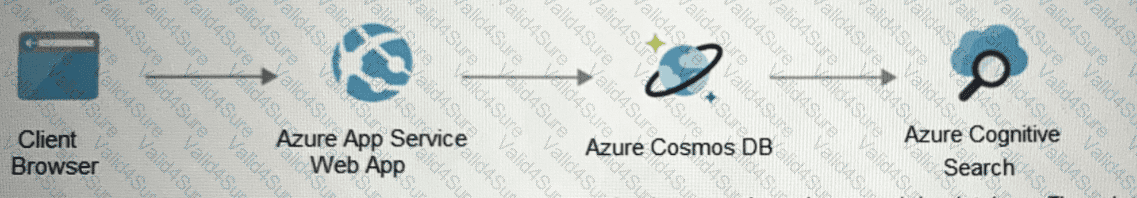
You need to provide recommendations to secure the connection between the web app and the database. The solution must follow the Zero Trust model.
Solution: You recommend creating private endpoints for the web app and the database layer.
Does this meet the goal?
You have a Microsoft 365 tenant. Your company uses a third-party software as a service (SaaS) app named App1. App1 supports authenticating users by using Azure AO credentials. You need to recommend a solution to enable users to authenticate to App1 by using their Azure AD credentials. What should you include in the recommendation?
You have an Azure subscription that contains the resources shown in the following table.

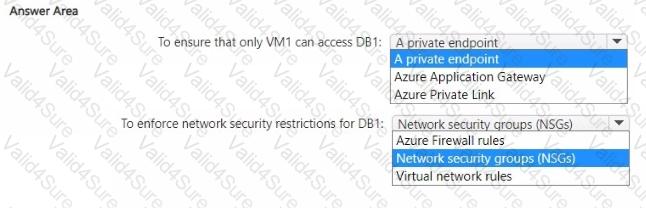
You need to recommend a network security solution for App1. The solution must meet the following requirements:
• Only the virtual machines that are connected to Subnet1 must be able to connect to D81.
• DB1 must be inaccessible from the internet
• Costs must be minimized.
What should you include in the recommendation? To answer, select the options in the answer area. NOTE: Each correct answer is worth one point.
You have a Microsoft 365 tenant that contains two groups named Group1 and Group2.
You use Microsoft Defender XDR to manage the tenants of your company's customers.
You need to ensure that the users in Group1 can perform security tasks in the tenant of each customer. The solution must meet the following requirements:
The Group1 users must only be assigned the Security Operator role for the customer tenants.
The users in Group2 must be able to assign the Security Operators role to the Group1 users for the customer tenants.
The use of guest accounts must be minimized.
Administrative effort must be minimized.
What should you include in the solution?