SCS-C01 Exam Dumps - AWS Certified Security - Specialty
You need to inspect the running processes on an EC2 Instance that may have a security issue. How can you achieve this in the easiest way possible. Also you need to ensure that the process does not interfere with the continuous running of the instance.
Please select:
Development teams in your organization use S3 buckets to store the log files for various applications hosted ir development environments in IAM. The developers want to keep the logs for one month for troubleshooting purposes, and then purge the logs. What feature will enable this requirement?
Please select:
A company requires that data stored in IAM be encrypted at rest. Which of the following approaches achieve this requirement? Select 2 answers from the options given below.
Please select:
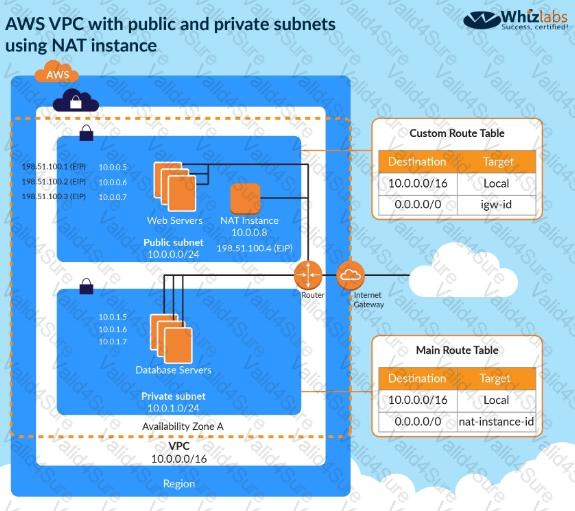
You have an Amazon VPC that has a private subnet and a public subnet in which you have a NAT instance server. You
have created a group of EC2 instances that configure themselves at startup by downloading a bootstrapping script
from S3 that deploys an application via GIT.
Which one of the following setups would give us the highest level of security?
Choose the correct answer from the options given below.
Please select:
You are planning on hosting a web application on IAM. You create an EC2 Instance in a public subnet. This instance needs to connect to an EC2 Instance that will host an Oracle database. Which of the following steps should be followed to ensure a secure setup is in place? Select 2 answers.
Please select:
You currently operate a web application In the IAM US-East region. The application runs on an auto-scaled layer of EC2 instances and an RDS Multi-AZ database. Your IT security compliance officer has tasked you to develop a reliable and durable logging solution to track changes made to your EC2.IAM and RDS resources. The solution must ensure the integrity and confidentiality of your log data. Which of these solutions would you recommend?
Please select:
You are working in the media industry and you have created a web application where users will be able to upload photos they create to your website. This web application must be able to call the S3 API in order to be able to function. Where should you store your API credentials whilst maintaining the maximum level of security?
Please select:
A company hosts data in S3. There is now a mandate that going forward all data in the S3 bucket needs to encrypt at rest. How can this be achieved?
Please select:
 C:\Users\wk\Desktop\mudassar\Untitled.jpg
C:\Users\wk\Desktop\mudassar\Untitled.jpg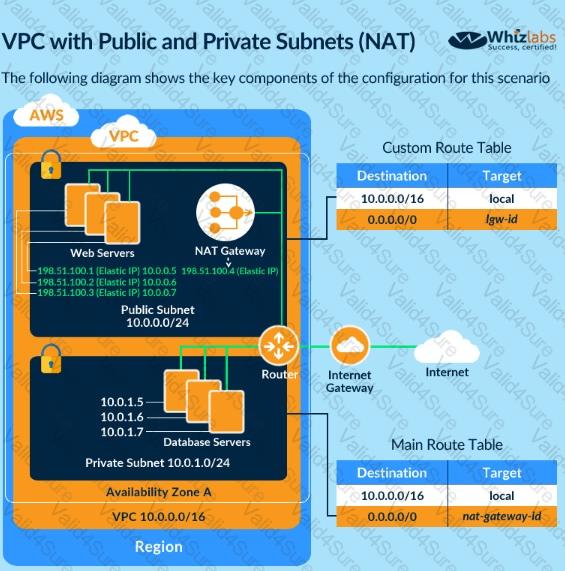 C:\Users\wk\Desktop\mudassar\Untitled.jpg
C:\Users\wk\Desktop\mudassar\Untitled.jpg