SPLK-1002 Exam Dumps - Splunk Core Certified Power User Exam
Searching for workable clues to ace the Splunk SPLK-1002 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s SPLK-1002 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
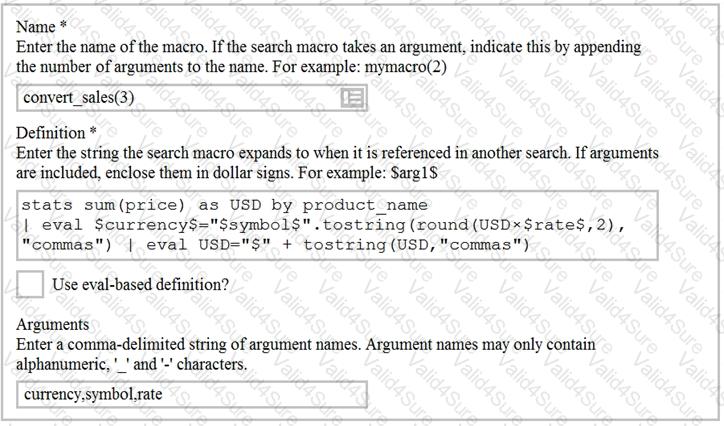
Based on the macro definition shown below, what is the correct way to execute the macro in a search string?
How is a Search Workflow Action configured to run at the same time range as the original search?
Which option of the transaction command would be used to specify the maximum time between events in a transaction?
A user wants to create a new field alias for a field that appears in two sourcetypes.
How many field aliases need to be created?
Which of the following statements describes this search?
sourcetype=access_combined I transaction JSESSIONID | timechart avg (duration)
The Field Extractor (FX) is used to extract a custom field. A report can be created using this custom field. The created report can then be shared with other people in the organization. If another person in the organization runs the shared report and no results are returned, why might this be? (select all that apply)