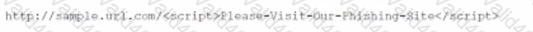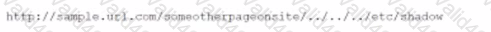SY0-601 Exam Dumps - CompTIA Security+ Exam 2023
Developers are writing code and merging it into shared repositories several times a day. where it is tested automatically. Which of the following concepts does this best represent?
Which of the following is performed to gain a better understanding of how specific devices are set up by identifying the arrangement of settings?
A cybersecurity analyst reviews the log files from a web server end sees a series of files that indicate a directory traversal attack has occurred Which of the following is the analyst most likely seeing?
A company decided to reduce the cost of its annual cyber insurance policy by removing the coverage for ransomware attacks. Which of the following analysis elements did the company most likely use in making this decision?
A company decided to reduce the cost of its annual cyber insurance policy by removing the coverage for ransomware attacks. Which of the following analysis elements did the company most likely use in making this decision?
A routine audit of medical billing claims revealed that several claims were submitted without the subscriber's knowledge A review of the audit logs for the medical billing company's system indicated a company employee downloaded customer records and adjusted the direct deposit information to a personal bank account Which of the following does this action describe?
A retail executive recently accepted a job with a major competitor. The following week, a security analyst reviews the security logs and identifies successful logon attempts to access the departed executive's accounts. Which of the following security practices would have addressed the issue?
Which of the following roles, according to the shared responsibility model, is responsible for securing the company's database in an laaS model for a cloud environment?
An organization is concerned that its hosted web servers are not running the most updated version of the software. Which of the following would work BEST to help identify potential vulnerabilities?