Note! Following 156-215.80 Exam is Retired now. Please select the alternative replacement for your Exam Certification.
156-215.80 Exam Dumps - Check Point Certified Security Administrator R80
Question # 10
Which the following type of authentication on Mobile Access can NOT be used as the first authentication method?
Question # 11
You find that Users are not prompted for authentication when they access their Web servers, even though you have created an HTTP rule via User Authentication. Choose the BEST reason why.
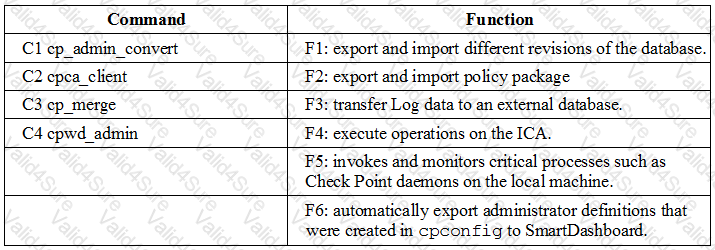
Question # 13
Match the following commands to their correct function. Each command has one function only listed.
Question # 14
When launching SmartDashboard, what information is required to log into R77?
Question # 15
You want to establish a VPN, using certificates. Your VPN will exchange certificates with an external partner. Which of the following activities sh you do first?