200-901 Exam Dumps - DevNet Associate (DEVASC)
A developer is attempting to retrieve all the messages from a Cisco Webex space. The server responds by sending the first 1,000 messages. The developer must make additional requests to retrieve the rest of the messages. Which API constraint is described in this scenario?
Refer to the exhibit.
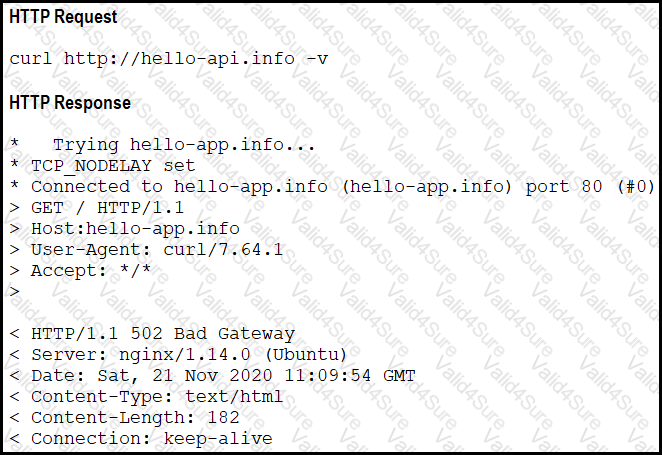
A developer cannot reach the web application behind an NGINX load balancer. The developer sends a request to an application FQDN with cURL but gets an HTTP 502 response. Which action solves the problem?
An engineer must review and clean up a code repository. During the review, the engineer finds a file named config.json that contains API URLs, shared keys, and other application configurations. Which two methods, according to best practice, must be used to protect secrets? (Choose two.)
Which type of OWASP threat forges a malicious HTTP request into an application?
A developer starts to learn about building applications that use Cisco APIs. The developer needs access to Cisco security products in a development lab to test the first new Dlication that has been built. Which DevNet resource must be used?
A REST API service requires authentication based on the username and password. The user “john†has the password “384279060†and the Base64 encoding of those credentials is “am9objowMTIzNDU2Nzg=â€. Which method completes an authentication request?