200-901 Exam Dumps - DevNet Associate (DEVASC)
What are two benefits of implementing common data structures when working with APIs in remote systems? (Choose two.)
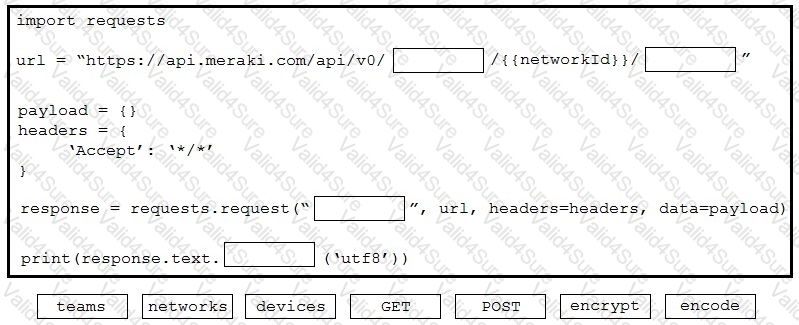
Drag and drop the code from the bottom onto the box where the code is missing to obtain a list of network devices by using the Cisco Meraki API. Not all options are used.
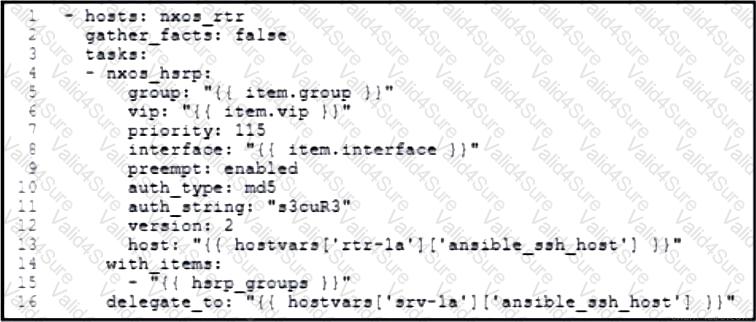
Refer to the exhibit. An engineer runs a network that consists of Cisco Nexus devices. The network is distributed between data centers in different locations. The switches are configured using standalone connections and a single point of failure. Which process is being automated by the Ansible playbook?
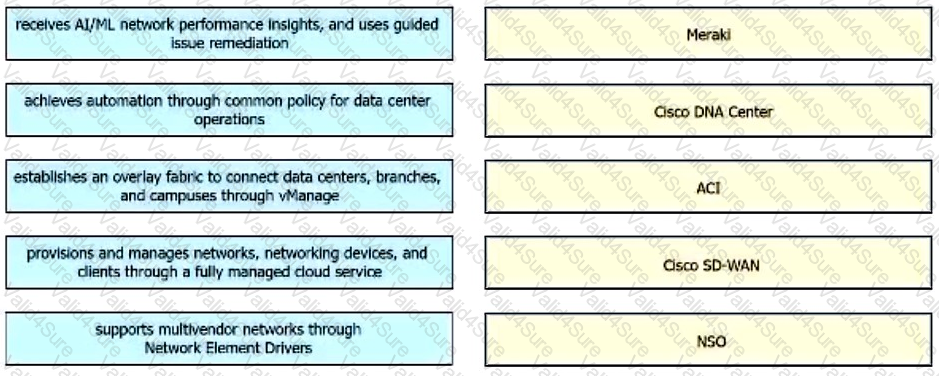
Drag and drop the capabilities from the left onto the Cisco Network Management Platforms that support the capabilities on the right.
A developer attempts to refactor and improve the application code. It is noticed that the code contains several pieces of key information that could be a security threat if this code is accessible by those who are not
authorized to this data. Which approach addresses the security concerns noticed by the developer?