200-901 Exam Dumps - DevNet Associate (DEVASC)
Refer to the exhibit.
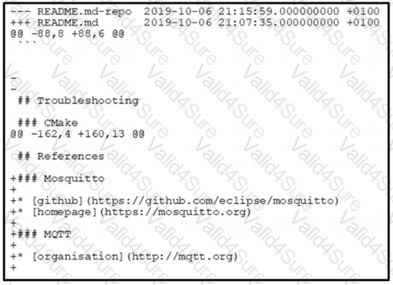
The output of the diff-u README.md-repo README.md command is shown. The original file was 165 lines long How many lines are in the edited copy of the file?
Refer to the exhibit.
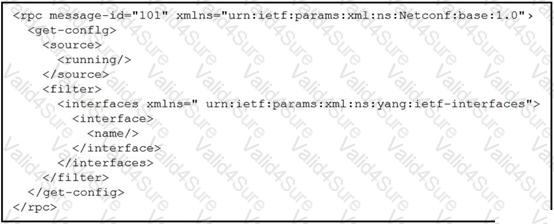
A network engineer uses model-driven programmability to monitor and perform changes on the network. The network engineer decides to use the NETCONF RPC message to complete one of their tasks. What is accomplished by sending the RPC message?
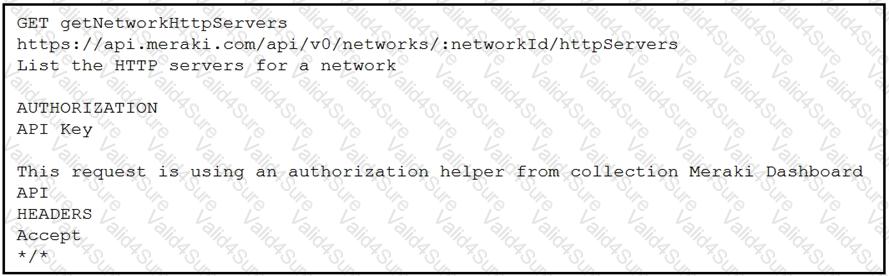
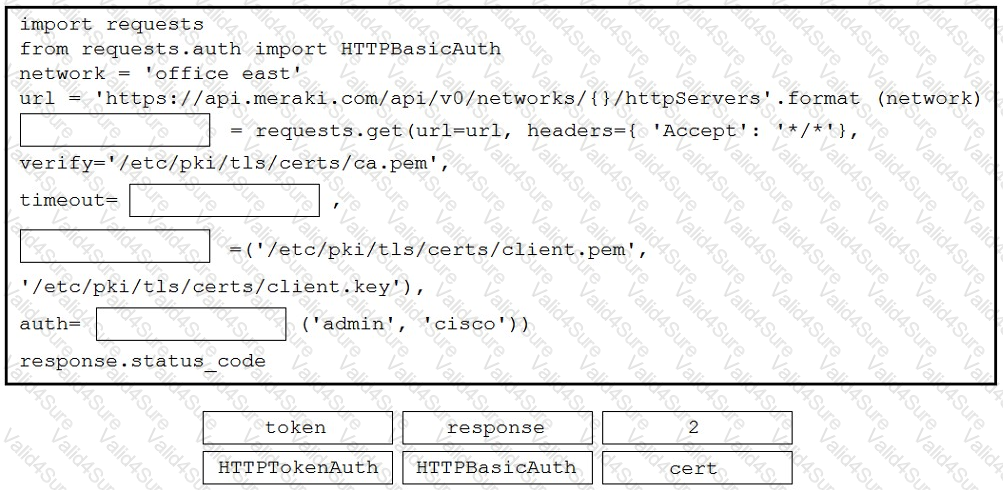
Refer to the exhibit. A developer is creating a Python script to obtain a list of HTTP servers on a network named office_east by using the Cisco Meraki API. The request has these requirements:
• Must time out if the response is not received within 2 seconds.
• Must utilize client certificates and SSL certificate verification.
• Must utilize basic authentication that uses a username of admin and a password of cisco.
• Must save the response to an object named response.
Drag and drop the code snippets from the bottom onto the blanks in the code to meet the requirements. Not all options are used.
In test-driven development, what are two of the green bar patterns? (Choose two.)
Refer to the exhibit.
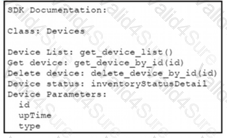
A Python script must delete all Cisco Catayst 9300 Series switches that have an uptime that is greater than 90 days The script must also query for the status of all the other devices Drag and drop the code from the bottom onto the bottom box the code is missing to complete the script Not at options are used

Drag and drop the code snippets from the bottom to the blanks in the code to complete the HTTP response. Not all options are used.
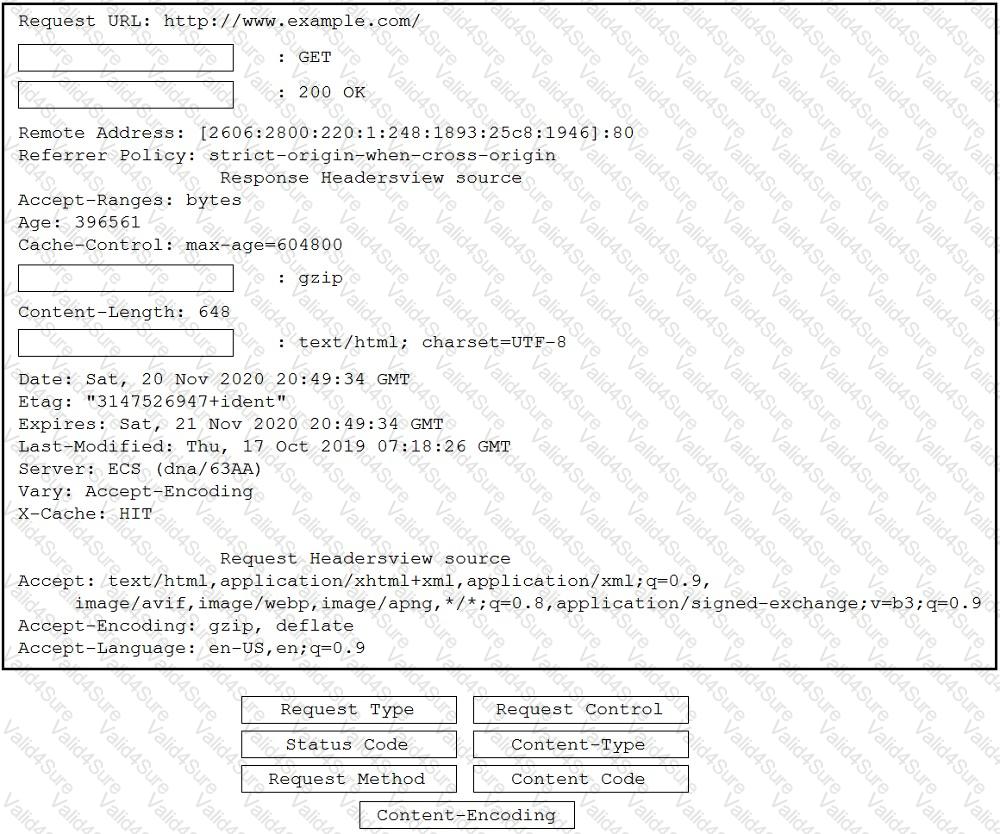
A developer is working on a feature for a new application. The changes in the existing branch named 'feat00304' must be integrated into a single commit with the current working primary branch named 'prodapp411926287'. Which git command must be used?
