312-38 Exam Dumps - Certified Network Defender (CND)
Searching for workable clues to ace the ECCouncil 312-38 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 312-38 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
The agency Jacob works for stores and transmits vast amounts of sensitive government data that cannot be compromised. Jacob has implemented Encapsulating Security Payload (ESP) to encrypt IP traffic. Jacob
wants to encrypt the IP traffic by inserting the ESP header in the IP datagram before the transport layer protocol header. What mode of ESP does Jacob need to use to encrypt the IP traffic?
The network administrator wants to strengthen physical security in the organization. Specifically, to
implement a solution stopping people from entering certain restricted zones without proper credentials.
Which of following physical security measures should the administrator use?
Fargo, head of network defense at Globadyne Tech, has discovered an undesirable process in several Linux systems, which causes machines to hang every 1 hour. Fargo would like to eliminate it; what
command should he execute?
James, a network admin in a large US based IT firm, was asked to audit and implement security
controls over all network layers to achieve Defense-in-Depth. While working on this assignment, James
has implemented both blacklisting and whitelisting ACLs. Which layer of defense-in-depth architecture is
Jason working on currently?
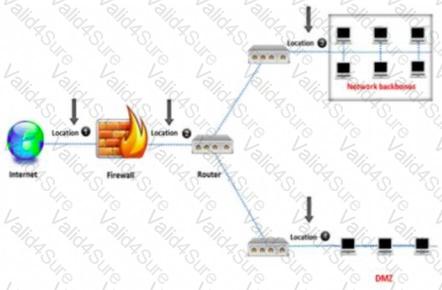
An administrator wants to monitor and inspect large amounts of traffic and detect unauthorized attempts from inside the organization, with the help of an IDS. They are not able to
recognize the exact location to deploy the IDS sensor. Can you help him spot the location where the IDS sensor should be placed?
A CCTV camera, which can be accessed on the smartphone from a remote location, is an example of _____
Which of the following indicators refers to potential risk exposures that attackers can use to breach the security of an organization?