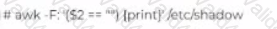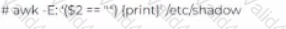312-38 Exam Dumps - Certified Network Defender (CND)
Searching for workable clues to ace the ECCouncil 312-38 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 312-38 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
John has been working a* a network administrator at an IT company. He wants to prevent misuse of accounts by unauthorized users. He wants to ensure that no accounts have empty passwords. Which of the following commands does John use to list all the accounts with an empty password?
Physical access controls help organizations monitor, record, and control access to the information assets and facility. Identify the category of physical security controls which includes security labels and
warning signs.
Which type of risk treatment process Includes not allowing the use of laptops in an organization to ensure its security?
Which wireless networking topology setup requires same channel name and SSID?
Stephanie is currently setting up email security so all company data is secured when passed through email. Stephanie first sets up encryption to make sure that a specific user's email is protected. Next, she needs to
ensure that the incoming and the outgoing mail has not been modified or altered using digital signatures. What is Stephanie working on?