CAS-005 Exam Dumps - CompTIA SecurityX Certification Exam
A security professional is investigating a trend in vulnerability findings for newly deployed cloud systems Given the following output:
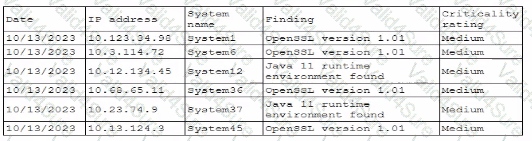
Which of the following actions would address the root cause of this issue?
A security analyst is reviewing the following authentication logs:
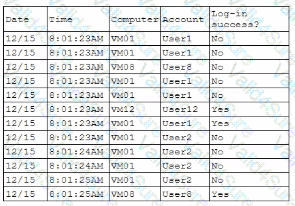
Which of the following should the analyst do first?
A company isolated its OT systems from other areas of the corporate network These systems are required to report usage information over the internet to the vendor Which oi the following b*st reduces the risk of compromise or sabotage' (Select two).
During a periodic internal audit, a company identifies a few new, critical security controls that are missing. The company has a mature risk management program in place, and the following requirements must be met:
The stakeholders should be able to see all the risks.
The risks need to have someone accountable for them.
Which of the following actions should the GRC analyst take next?
A company that uses containers to run its applications is required to identify vulnerabilities on every container image in a private repository The security team needs to be able to quickly evaluate whether to respond to a given vulnerability Which of the following, will allow the security team to achieve the objective with the last effort?
The identity and access management team is sending logs to the SIEM for continuous monitoring. The deployed log collector is forwarding logs to
the SIEM. However, only false positive alerts are being generated. Which of the following is the most likely reason for the inaccurate alerts?
An organization has been using self-managed encryption keys rather than the free keys managed by the cloud provider. The Chief Information Security Officer (CISO) reviews the monthly bill and realizes the self-managed keys are more costly than anticipated. Which of the following should the CISO recommend to reduce costs while maintaining a strong security posture?
Which of the following are risks associated with vendor lock-in? (Select two).