CAS-005 Exam Dumps - CompTIA SecurityX Certification Exam
A security engineer must resolve a vulnerability in a deprecated version of Python for a custom-developed flight simul-ation application that is monitored and controlled remotely. The source code is proprietary and built with Python functions running on the Ubuntu operating system. Version control is not enabled for the application in development or production. However, the application must remain online in the production environment using built-in features. Which of the following solutions best reduces the attack surface of these issues and meets the outlined requirements?
A security analyst wants to use lessons learned from a poor incident response to reduce dwell lime in the future The analyst is using the following data points
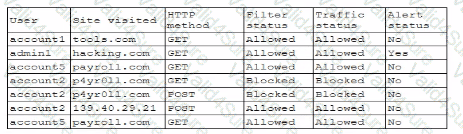
Which of the following would the analyst most likely recommend?
A security analyst is reviewing suspicious log-in activity and sees the following data in the SICM:
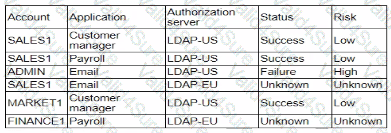
Which of the following is the most appropriate action for the analyst to take?
A company wants to use loT devices to manage and monitor thermostats at all facilities The thermostats must receive vendor security updates and limit access to other devices within the organization Which of the following best addresses the company's requirements''
An analyst has prepared several possible solutions to a successful attack on the company. The solutions need to be implemented with the least amount of downtime. Which of the following should the analyst perform?
A company migrating to a remote work model requires that company-owned devices connect to a VPN before logging in to the device itself. The VPN gateway requires that a specific key extension is deployed to the machine certificates in the internal PKI. Which of the following best explains this requirement?
A developer makes a small change to a resource allocation module on a popular social media website and causes a memory leak. During a peak utilization period, several web servers crash, causing the website to go offline. Which of the following testing techniques is the most efficient way to prevent this from reoccurring?
Which of the following best explains the business requirement a healthcare provider fulfills by encrypting patient data at rest?