CFR-210 Exam Dumps - Logical Operations CyberSec First Responder
Searching for workable clues to ace the Logical Operations CFR-210 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s CFR-210 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
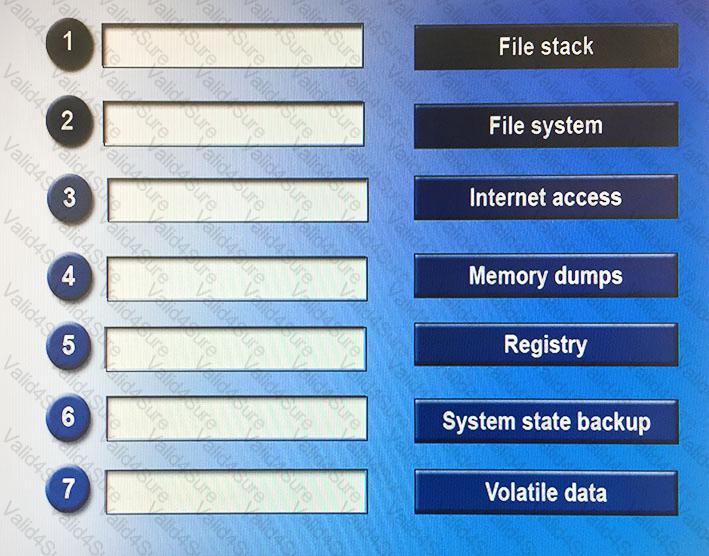
Drag and drop the following steps in the correct order from first (1) to last (7) that a forensic expert would follow based on data analysis in a Windows system.
A system administrator is informed that a user received an email containing a suspicious attachment. Which of the following methods is the FASTEST way to determine whether the file is suspicious or not?
An attacker has sent malicious macro-enabled Office files. Which of the following regular expressions will return a list of macro-enabled files?
During an annual penetration test, several rootkit-enabled systems are found to be exfiltrating data. The penetration test team and the internal incident response team work to begin cleanup. The company’s operations team offers a new emails server to use for communications during the incident. As cleanup continues, the attackers seem to know exactly what the incident response plan is. Which of the following will prevent the attackers from compromising cleanup activities?