CS0-001 Exam Dumps - CompTIA CySA+ Certification Exam
A technician receives a report that a user’s workstation is experiencing no network connectivity. The technician investigates and notices the patch cable running the back of the user’s VoIP phone is routed directly under the rolling chair and has been smashed flat over time.
Which of the following is the most likely cause of this issue?
A system administrator who was using an account with elevated privileges deleted a large amount of log files generated by a virtual hypervisor in order to free up disk space. These log files are needed by the security team to analyze the health of the virtual machines. Which of the following compensating controls would help prevent this from reoccurring? (Select two.)
A vulnerability scan has returned the following information:
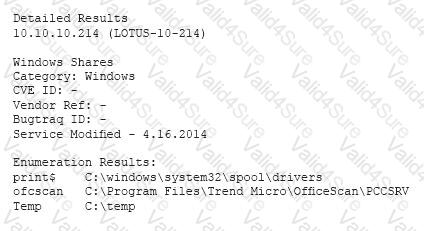
Which of the following describes the meaning of these results?
An HR employee began having issues with a device becoming unresponsive after attempting to open an email attachment. When informed, the security analyst became suspicious of the situation, even though there was not any unusual behavior on the IDS or any alerts from the antivirus software. Which of the following BEST describes the type of threat in this situation?
An analyst wants to use a command line tool to identify open ports and running services on a host along with the application that is associated with those services and port. Which of the following should the analyst use?
An application development company released a new version of its software to the public. A few days after the release, the company is notified by end users that the application is notably slower, and older security bugs have reappeared in the new release. The development team has decided to include the security analyst during their next development cycle to help address the reported issues. Which of the following should the security analyst focus on to remedy the existing reported problems?
After running a packet analyzer on the network, a security analyst has noticed the following output:
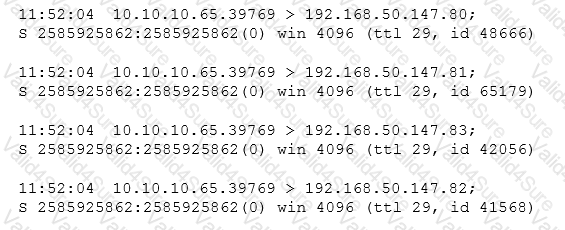
Which of the following is occurring?
After analyzing and correlating activity from multiple sensors, the security analyst has determined a group from a high-risk country is responsible for a sophisticated breach of the company network and continuous administration of targeted attacks for the past three months. Until now, the attacks went unnoticed. This is an example of: