CS0-001 Exam Dumps - CompTIA CySA+ Certification Exam
Law enforcement has contacted a corporation’s legal counsel because correlated data from a breach shows the organization as the common denominator from all indicators of compromise. An employee overhears the conversation between legal counsel and law enforcement, and then posts a comment about it on social media. The media then starts contacting other employees about the breach. Which of the following steps should be taken to prevent further disclosure of information about the breach?
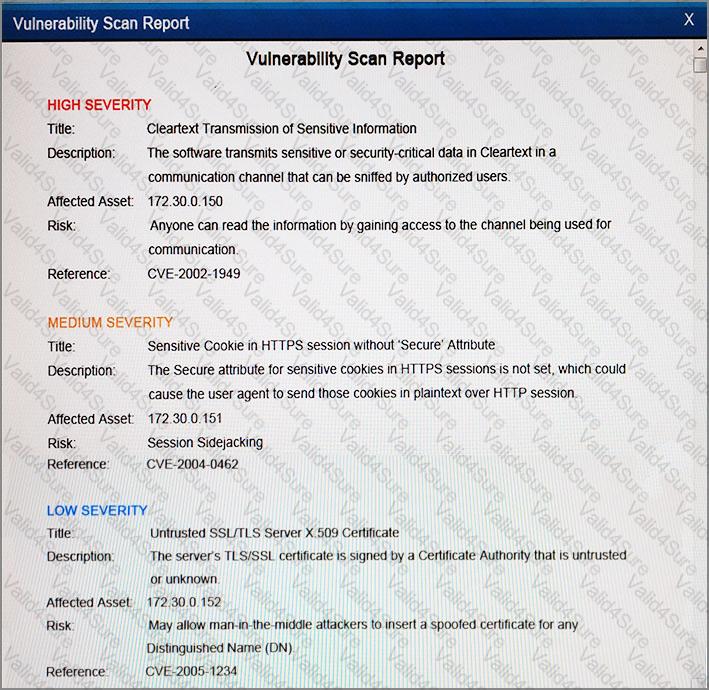
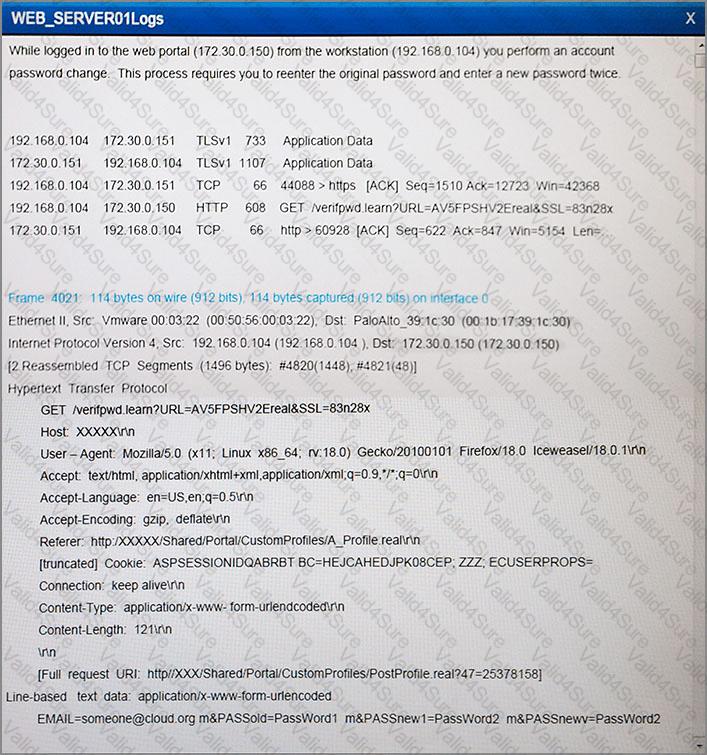
The developers recently deployed new code to three web servers. A daily automated external device scan report shows server vulnerabilities that are failing items according to PCI DSS.
If the vulnerability is not valid, the analyst must take the proper steps to get the scan clean.
If the vulnerability is valid, the analyst must remediate the finding.
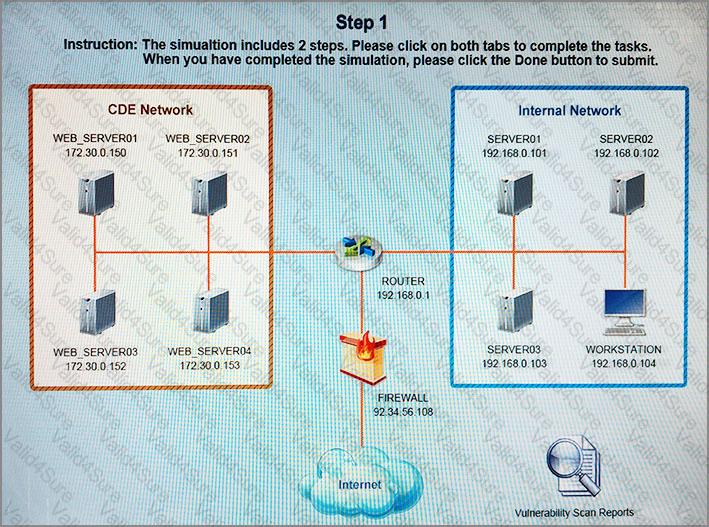
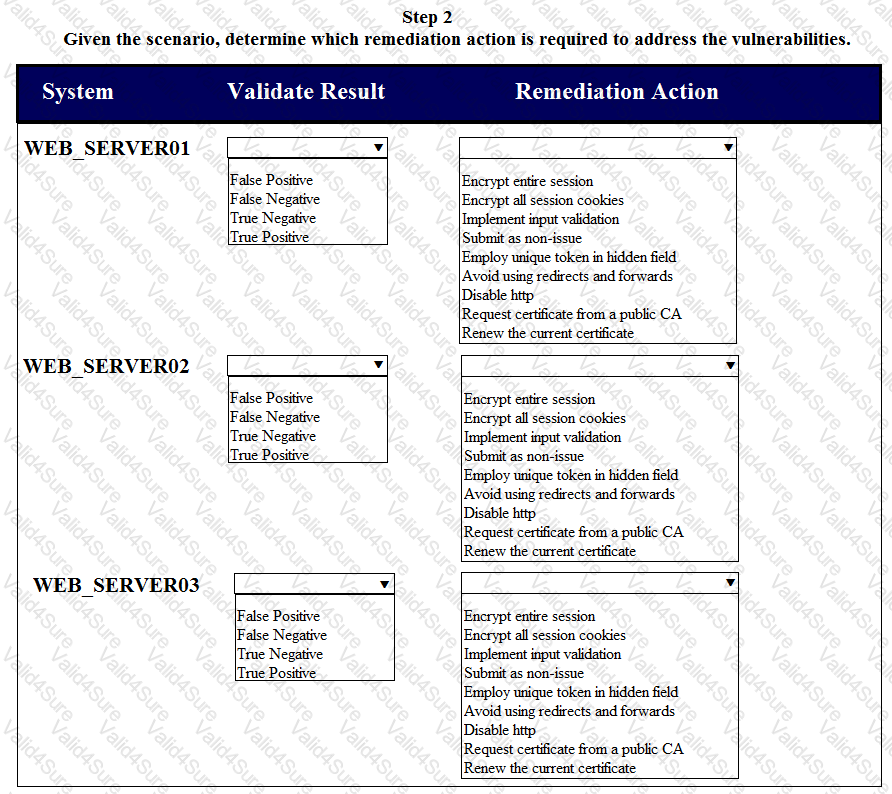
After reviewing the information provided in the network diagram, select the STEP 2 tab to complete the simulation by selecting the correct Validation Result and Remediation Action for each server listed using the drop-down options.
Instructions
STEP 1: Review the information provided in the network diagram.
STEP 2: Given the scenario, determine which remediation action is required to address the vulnerability.
If at any time you would like to bring back the initial state of the simulation, please select the Reset All button.
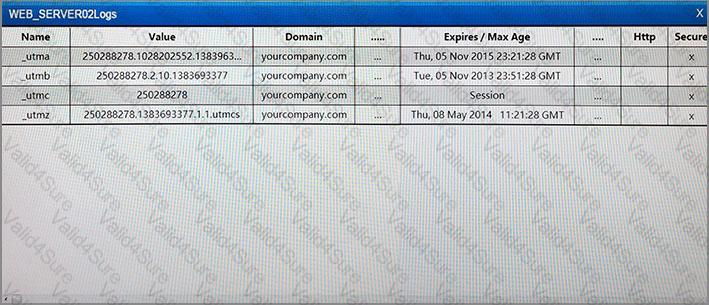
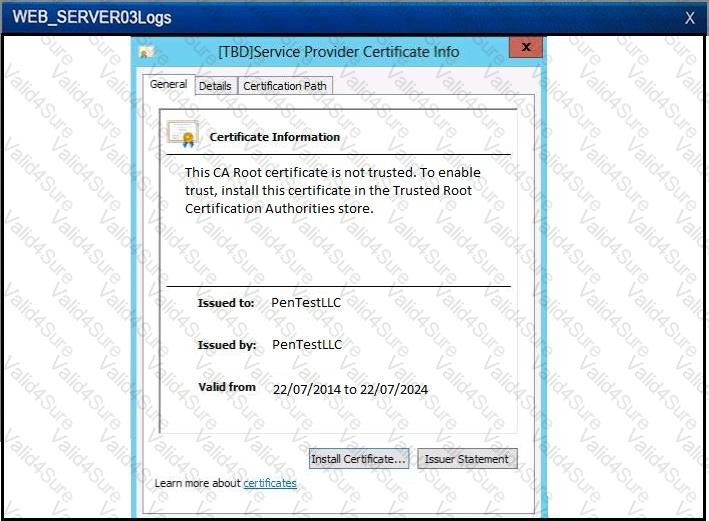
An alert has been distributed throughout the information security community regarding a critical Apache vulnerability. Which of the following courses of action would ONLY identify the known vulnerability?
The help desk informed a security analyst of a trend that is beginning to develop regarding a suspicious email that has been reported by multiple users. The analyst has determined the email includes an attachment named invoice.zip that contains the following files:
Locky.js
xerty.ini
xerty.lib
Further analysis indicates that when the .zip file is opened, it is installing a new version of ransomware on the devices. Which of the following should be done FIRST to prevent data on the company NAS from being encrypted by infected devices?
While a threat intelligence analyst was researching an indicator of compromise on a search engine, the web proxy generated an alert regarding the same indicator. The threat intelligence analyst states that related sites were not visited but were searched for in a search engine. Which of the following MOST likely happened in this situation?
Which of the following items represents a document that includes detailed information on when an incident was detected, how impactful the incident was, and how it was remediated, in addition to incident response effectiveness and any identified gaps needing improvement?
A security analyst is reviewing packet captures to determine the extent of success during an attacker’s reconnaissance phase following a recent incident.
The following is a hex and ASCII dump of one such packet:
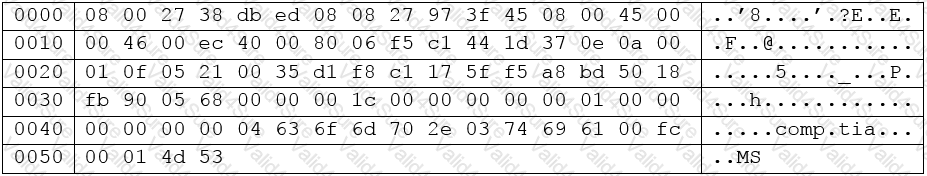
Which of the following BEST describes this packet?
A cybersecurity analyst is hired to review the security measures implemented within the domain controllers of a company. Upon review, the cybersecurity analyst notices a brute force attack can be launched against domain controllers that run on a Windows platform. The first remediation step implemented by the cybersecurity analyst is to make the account passwords more complex. Which of the following is the NEXT remediation step the cybersecurity analyst needs to implement?