FCP_FAZ_AN-7.4 Exam Dumps - FCP - FortiAnalyzer 7.4 Analyst
Searching for workable clues to ace the Fortinet FCP_FAZ_AN-7.4 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s FCP_FAZ_AN-7.4 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Exhibit.
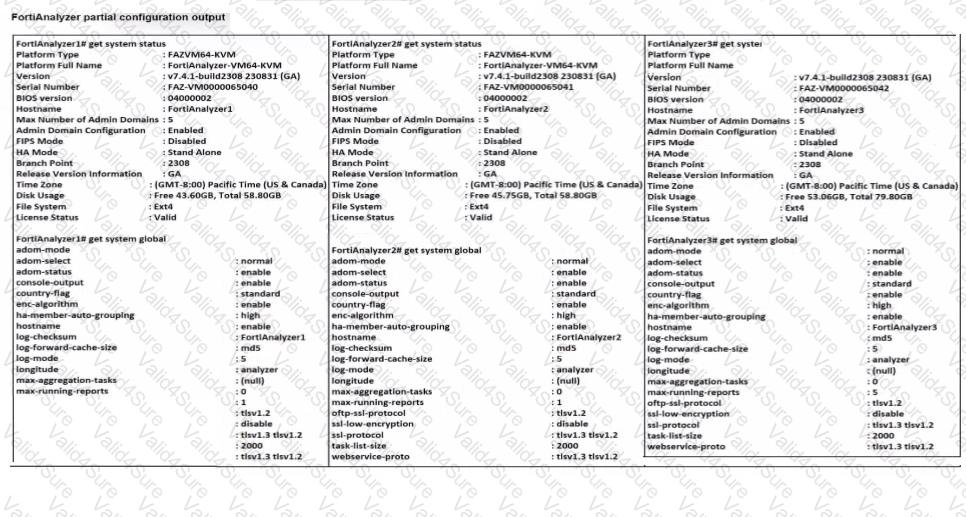
Based on the partial outputs displayed, which devices can be members of a FotiAnalyzer Fabric?
Which SQL query is in the correct order to query to database in the FortiAnalyzer?
What is the purpose of using data selectors when configuring event handlers?
Which two actions should an administrator take to vide Compromised Hosts on FortiAnalyzer? (Choose two.)
You created a playbook on FortiAnalyzer that uses a FortiOS connector.
When configuring the FortiGate side, which type of trigger must be used so that the actions in an automation stich are available in the FortiOS connector?
Which two statements about local logs on FortiAnalyzer are true? (Choose two.)