FCP_FAZ_AN-7.4 Exam Dumps - FCP - FortiAnalyzer 7.4 Analyst
Question # 5
You find that as part of your role as an analyst, you frequently search log View using the same parameters.
Instead of defining your search filters repeatedly, what can you do to save time?
Question # 7
Exhibit.
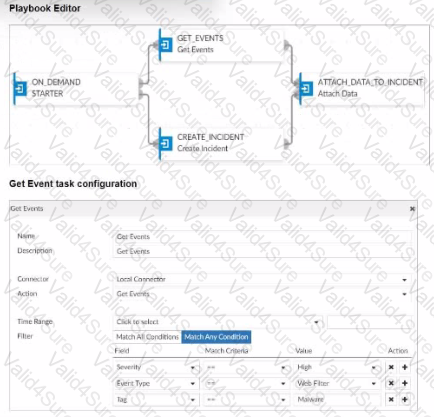
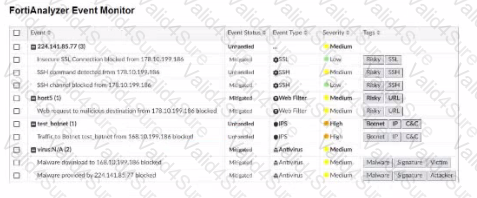
Assume these are all the events that exist on the FortiAnalyzer device.
How many events will be added to the incident created after running this playbook?
Question # 8
You must find a specific security event log in the FortiAnalyzer logs displayed in FortiView, but, so far, you have been uncuccessful.
Which two tasks should you perform to investigate why you are having this issue? (Choose two.)
