FCSS_ADA_AR-6.7 Exam Dumps - FCSS Advanced Analytics 6.7 Architect
Refer to the exhibit.
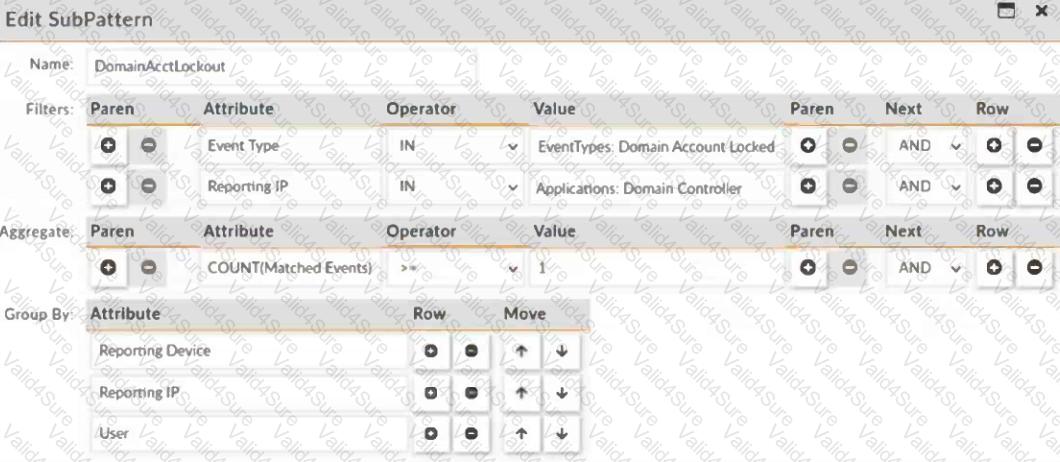
Consider the five account locked events received by FortiSIEM from domain controllers within the last 10 minutes (ten minutes is the evaluation window for the subpattern DomainAcctLockout):
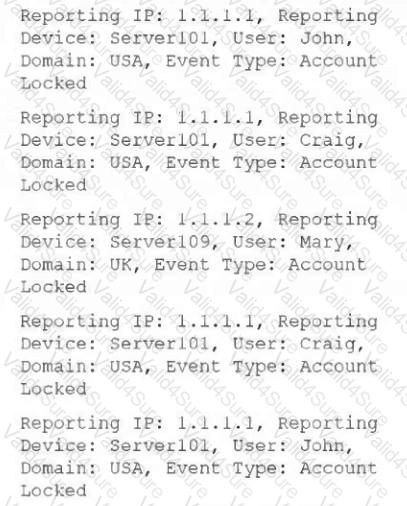
If you look for one or more matching events and groupings by the same reporting IP address, reporting device, and user, how many incidents are created?
In the event of a WAN link failure between the collector and the supervisor, by default, what is the maximum number of event files stored on the collector?
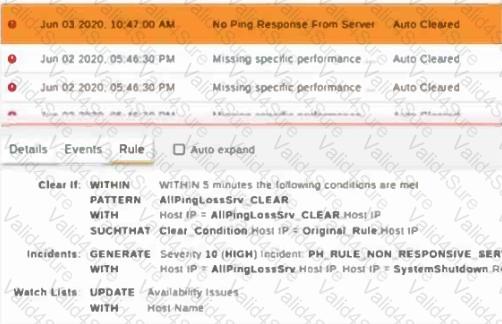
Refer to the exhibit.
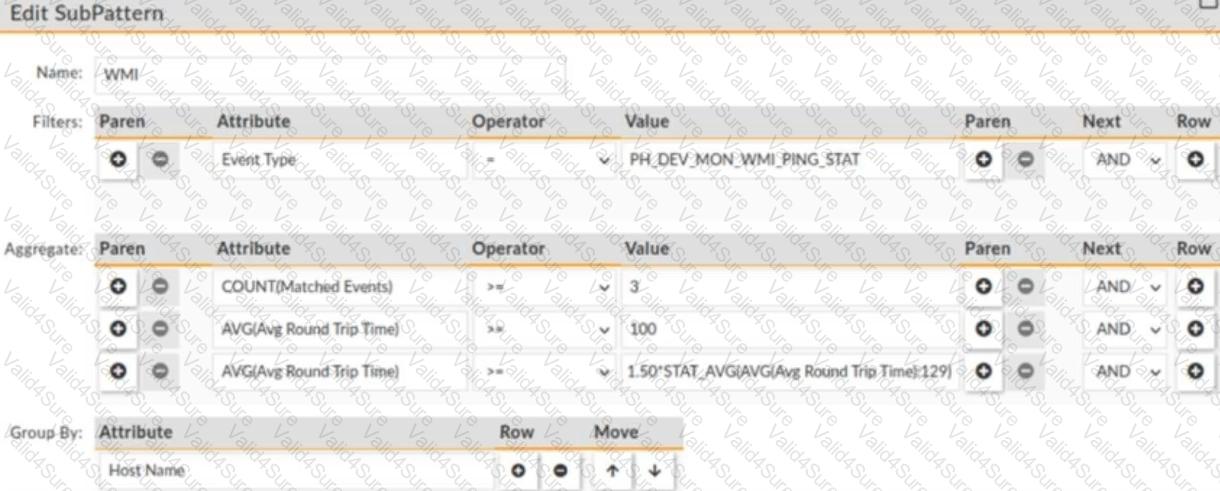
The window for this rule is 30Â minutes.
What is this rule tracking?
Refer to the exhibit.
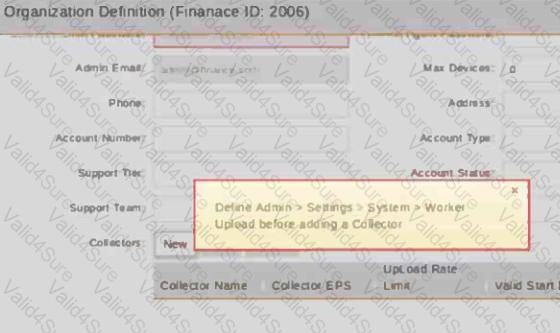
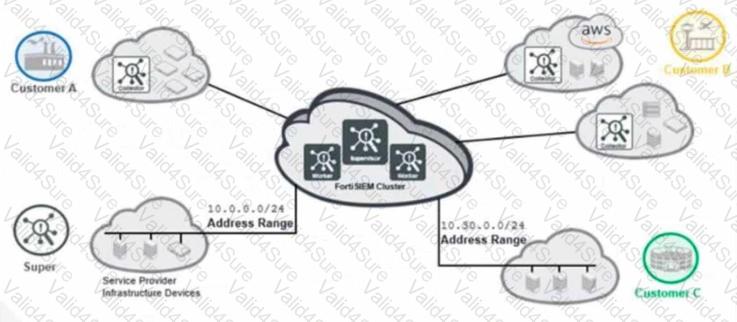
A service provider does not have a dedicated worker in the cluster, but still wants to add a collector to an organization.
What option does the administrator have?
Refer to the exhibit.
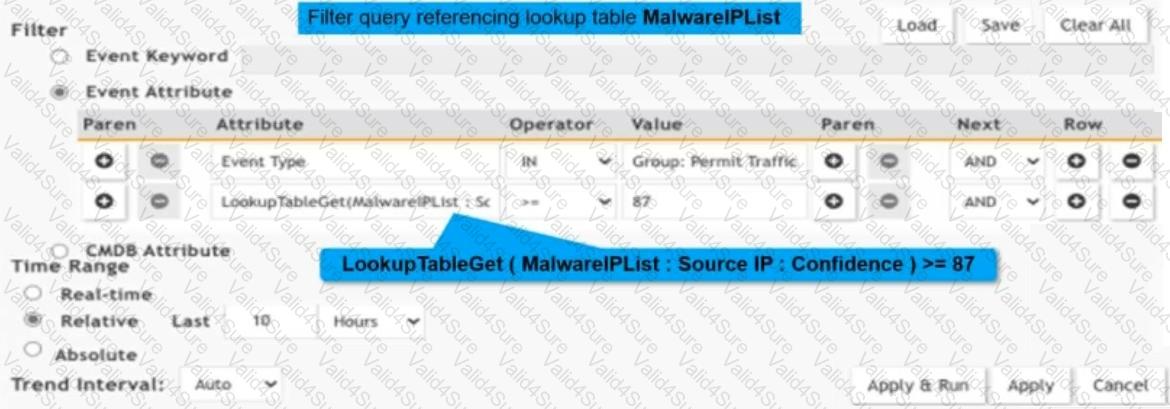
Consider a custom lookup tableMalwareIPList. An analyst constructed an analytic query to reference theMalwareIPListlookup table.
What is the outcome of the analytic query?