H12-831_V1.0 Exam Dumps - HCIP-Datacom-Advanced Routing & Switching Technology V1.0
Searching for workable clues to ace the Huawei H12-831_V1.0 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s H12-831_V1.0 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
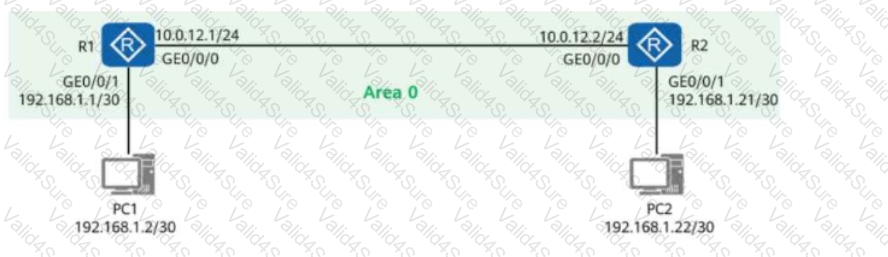
A network engineer provides a troubleshooting report after rectifying a fault. The actual network is simplified into the one shown in the figure, where:
R1 and R2 both have OSPF enabled.
R1 and R2 function as the gateways for PC1 and PC2, respectively.
Given this, which of the following statements are true?
Options:
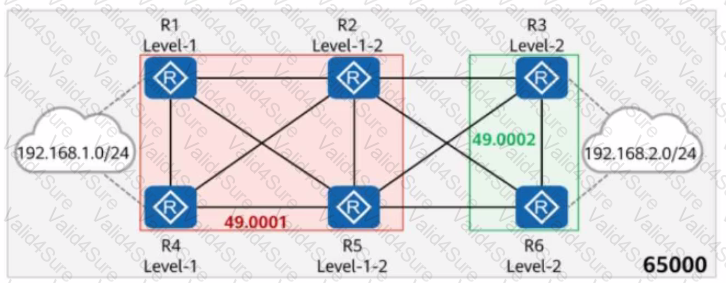
On the network shown in the figure, IS-IS runs on Rl, R2, R4, and R5, and the area ID is 49.0001. IS-IS runs on R3 and R6, and the area ID is 49.0002. In AS 65000, Ri, R3, R4, and R6 each establish IBGP peer relationships with R2 and R5. R2 and R5 are RRs, and Rl, R4, R3, and R6 are clients. The IBGP peer relationships are established using LoopbackO. The IP address of LoopbackO on each router is 10.0.X.X/32, and the router ID is 10.0.X.X, where X is the number of the router. Rl and R4 import the external route 192.168.1.0/24 to BGP through the import-route command, and R3 and R6 import the external route 192.168.2.0/24 to BGP through the import-route command. Which of the following statements are true?
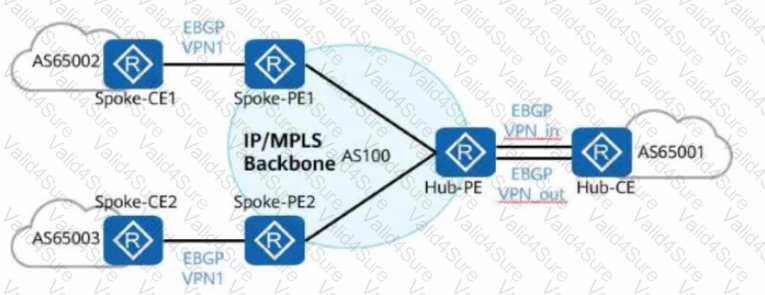
In the hub-spoke networking shown in the figure, the Hub-PE can be configured to allow repetitive local AS numbers for correct route transmission.
If the migration preparation is insufficient, which of the following problems may occur?
Options (Multiple Choice):
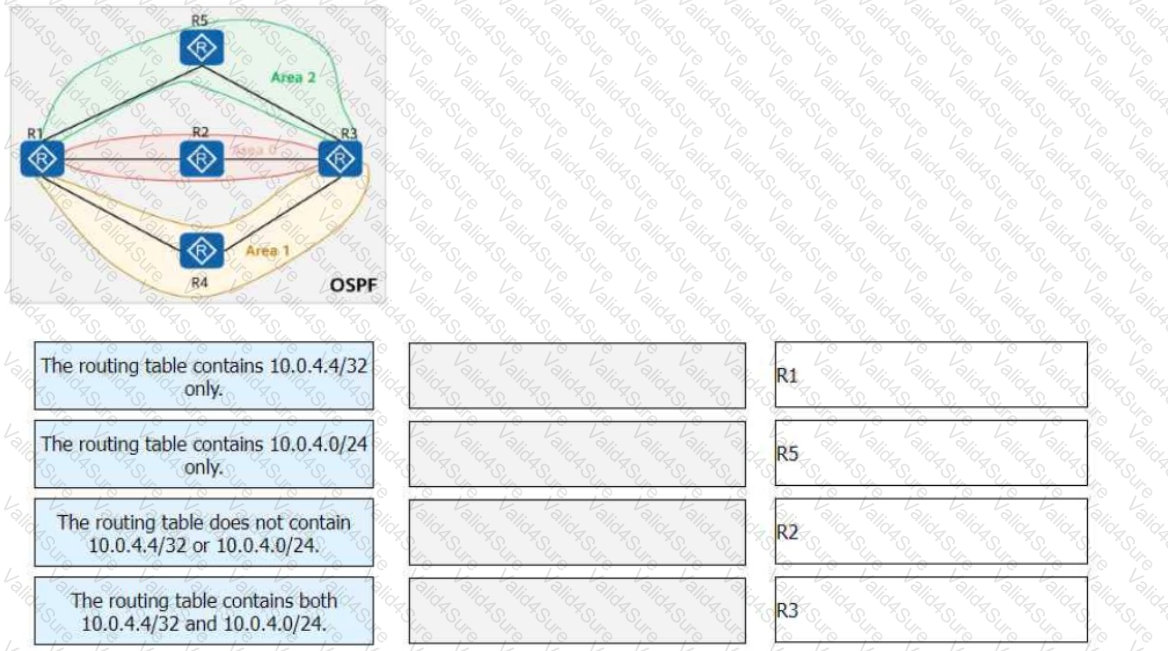
On the OSPF network shown in the figure, area 1 is an NSSA, area 2 is a stub area, and R4 imports an external route 10.0.4.4/32. The router ID of each router is 10.0.X.X, where X is the router number. The asbr-summary 10.0.4.0 255.255.255.0 command is configured in the OSPF processes of R1 and R3.
Match the following descriptions of routing tables with the corresponding routers:
On the network shown in the figure, IS-IS runs on R1, R2, R4, and R5, and the area ID is 49.0001. IS-IS runs on R3 and R6, and the area ID is 49.0002. The import-route isis level-2 into level-1 command is configured on R2.
In AS 65000, R1, R3, R4, and R6 each establish iBGP peer relationships with R2 and R5. R2 and R5 are Route Reflectors (RRs), and R1, R4, R3, and R6 are clients.
The iBGP peer relationships are established using Loopback0. The IP address of Loopback0 on each router is 10.0.X.X/32, and the router ID is 10.0.X.X, where X is the number of the router.
R1 and R4 import the external route 192.168.1.0/24 to BGP through the import-route command, and R3 and R6 import the external route 192.168.2.0/24 to BGP through the import-route command.
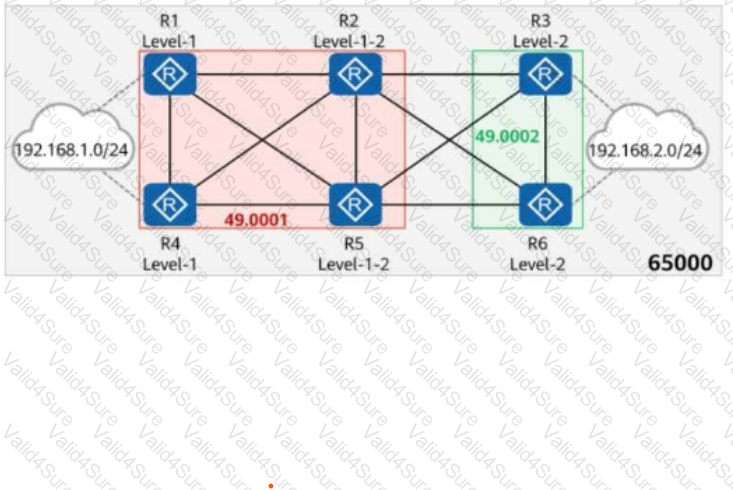
Which of the following statements are true?
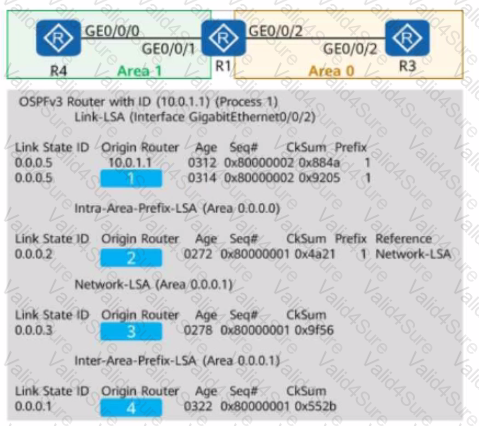
On the OSPFv3 network shown in the figure, OSPFv3 parameters use default values. The LSDB is checked on one of the devices. The router IDs of R1, R3, and R4 are 10.0.1.1, 10.0.3.3, and 10.0.4.4, respectively. The Origin Router part of some LSAs is hidden. Complete this part. (Tokens can be reused.)

The figure shows an MPLS packet with multiple labels.
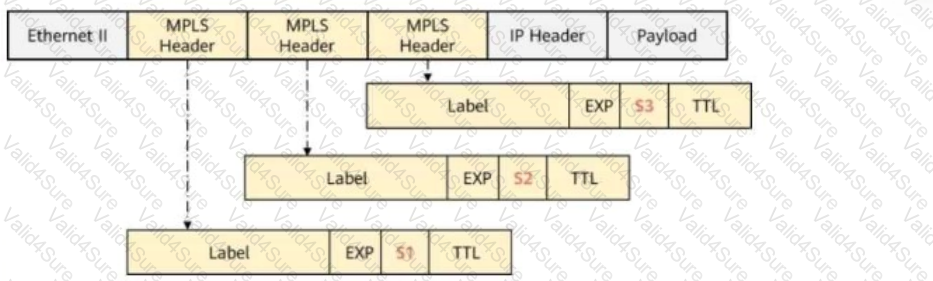
Which of the following values for the S field is correct?
