H12-831_V1.0 Exam Dumps - HCIP-Datacom-Advanced Routing & Switching Technology V1.0
Searching for workable clues to ace the Huawei H12-831_V1.0 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s H12-831_V1.0 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
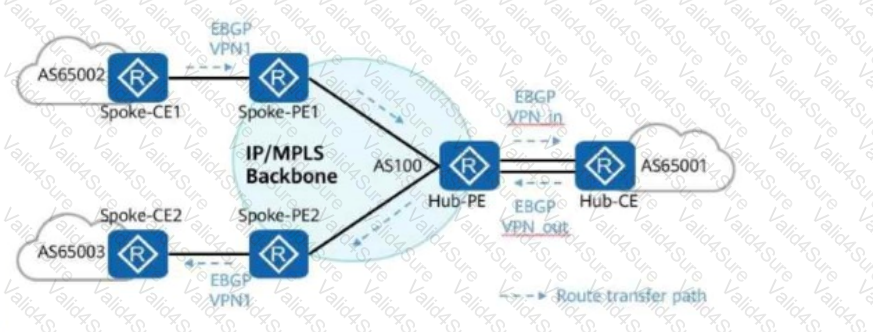
In the hub-spoke networking shown in the figure, which of the following commands must be configured on the Hub-PE to ensure correct route transmission?
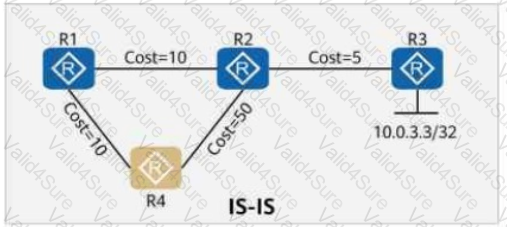
On the OSPF network shown in the figure, the cost values of links are marked. IS-IS Auto FRR is enabled on R1. The primary path from R1 to 10.0.3.3/32 is R1 → R2 → R3, and the backup path is R1 → R4 → R2 → R3.
Is this statement TRUE or FALSE?
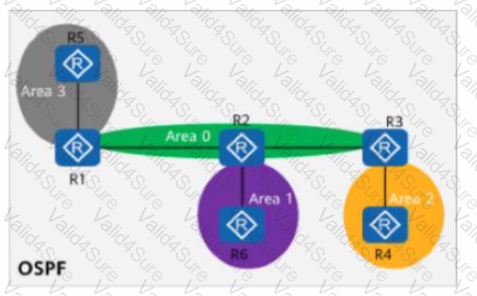
On the OSPF network shown in the figure, area 1 is a stub area, area 2 is a totally stub area, and area 3 is an NSSA. Which of the following LSAs does not exist in areas 1, 2, and 3?
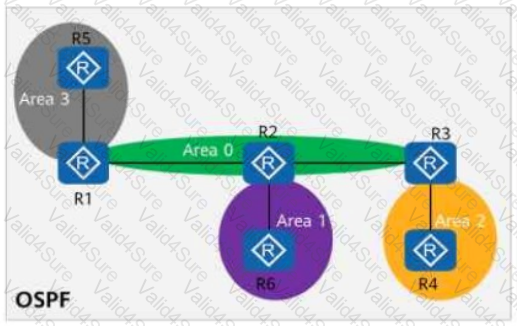
On the OSPF network shown in the figure, area 1 is a stub area, area 2 is a totally stub area, and area 3 is an NSSA. Which of the following routers are unable to import external routes?
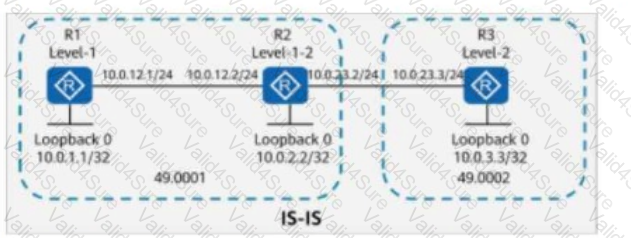
On the IS-IS network shown in the figure, R1 imports a default route using the default-route-advertise always level-1 command. Which of the following statements is false?
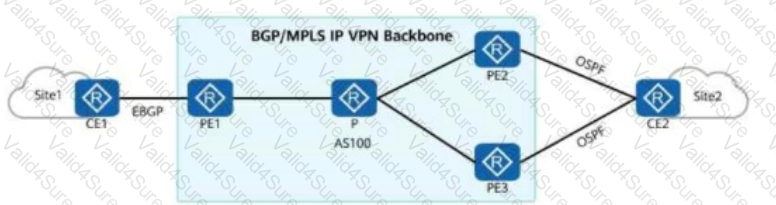
On an enterprise network shown in the figure, if CE2 is dual-homed to PE2 and PE3, a routing loop may occur during the exchange of Type 5 LSAs (External LSAs in OSPF).
To prevent the loop, the route-tag command can be run on PE2 and PE3.
In this way, if the route tag of the route received by PE3 is the same as that configured locally, the route is ignored.
Is this statement True or False?