NSE6_FNC-7.2 Exam Dumps - Fortinet NSE 6 - FortiNAC 7.2
Searching for workable clues to ace the Fortinet NSE6_FNC-7.2 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s NSE6_FNC-7.2 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which two things must be done to allow FortiNAC to process incoming syslog messages from an unknown vendor? (Choose two.)
In a wireless integration, what method does FortiNAC use to obtain connecting MAC address information?
View the command and output shown in the exhibit.
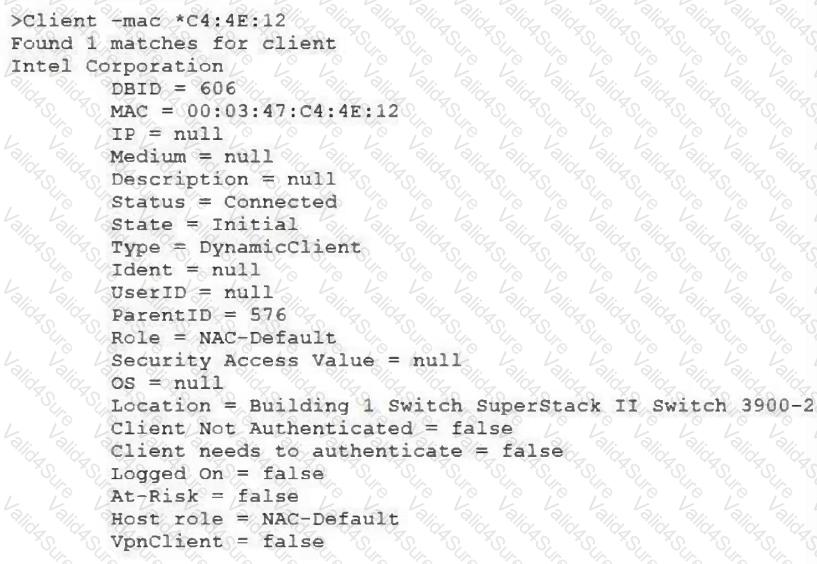
What is the current state of this host?
Which two of the following are required for endpoint compliance monitors? (Choose two.)