NSE7_SDW-7.2 Exam Dumps - Fortinet NSE 7 - SD-WAN 7.2
What are two reasons for using FortiManager to organize and manage the network for a group of FortiGate devices? (Choose two.)
What are two advantages of using an IPsec recommended template to configure an IPsec tunnel in a hub-and-spoke topology? (Choose two.)
What are two benefits of using the Internet service database (ISDB) in an SD-WAN rule? (Choose two.)
Which two statements about SLA targets and SD-WAN rules are true? (Choose two.)
Refer to the exhibit.
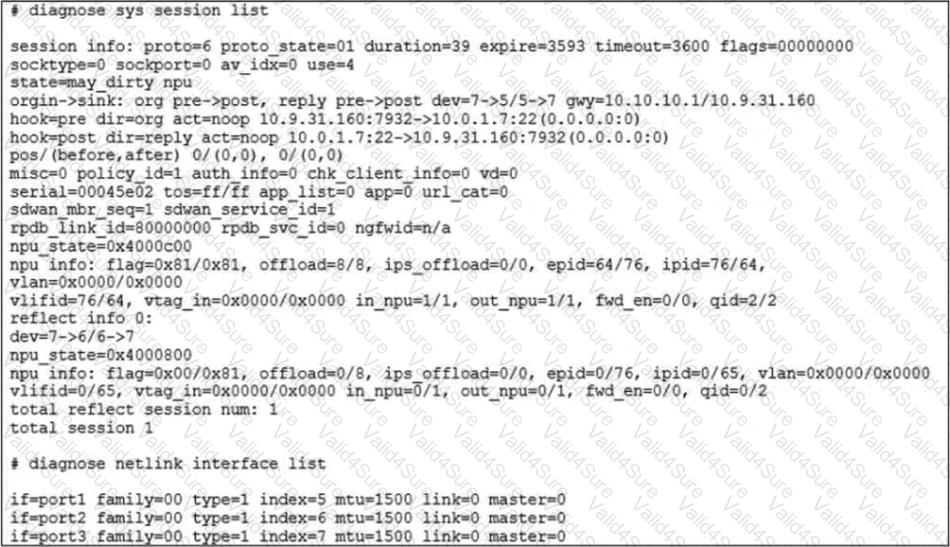
The exhibit shows the details of a session and the index numbers of some relevant interfaces on a FortiGate appliance that supports hardware offloading. Based on the information shown in the exhibits, which two statements about the session are true? (Choose two.)
Which two statements reflect the benefits of implementing the ADVPN solution to replace conventional VPN topologies? (Choose two.)
Refer to the exhibits.
Exhibit A -
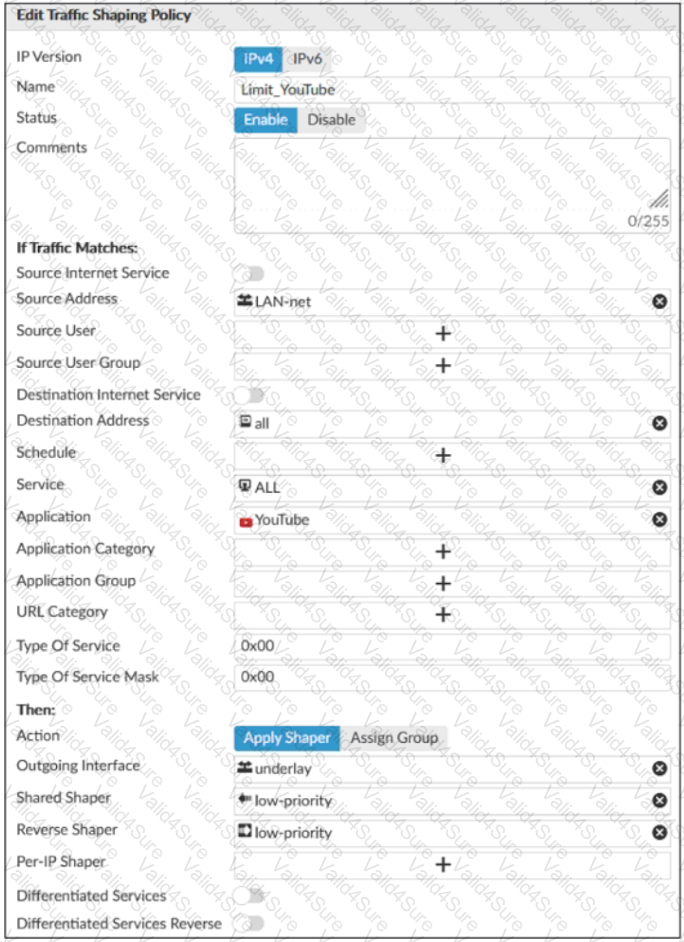
Exhibit B -
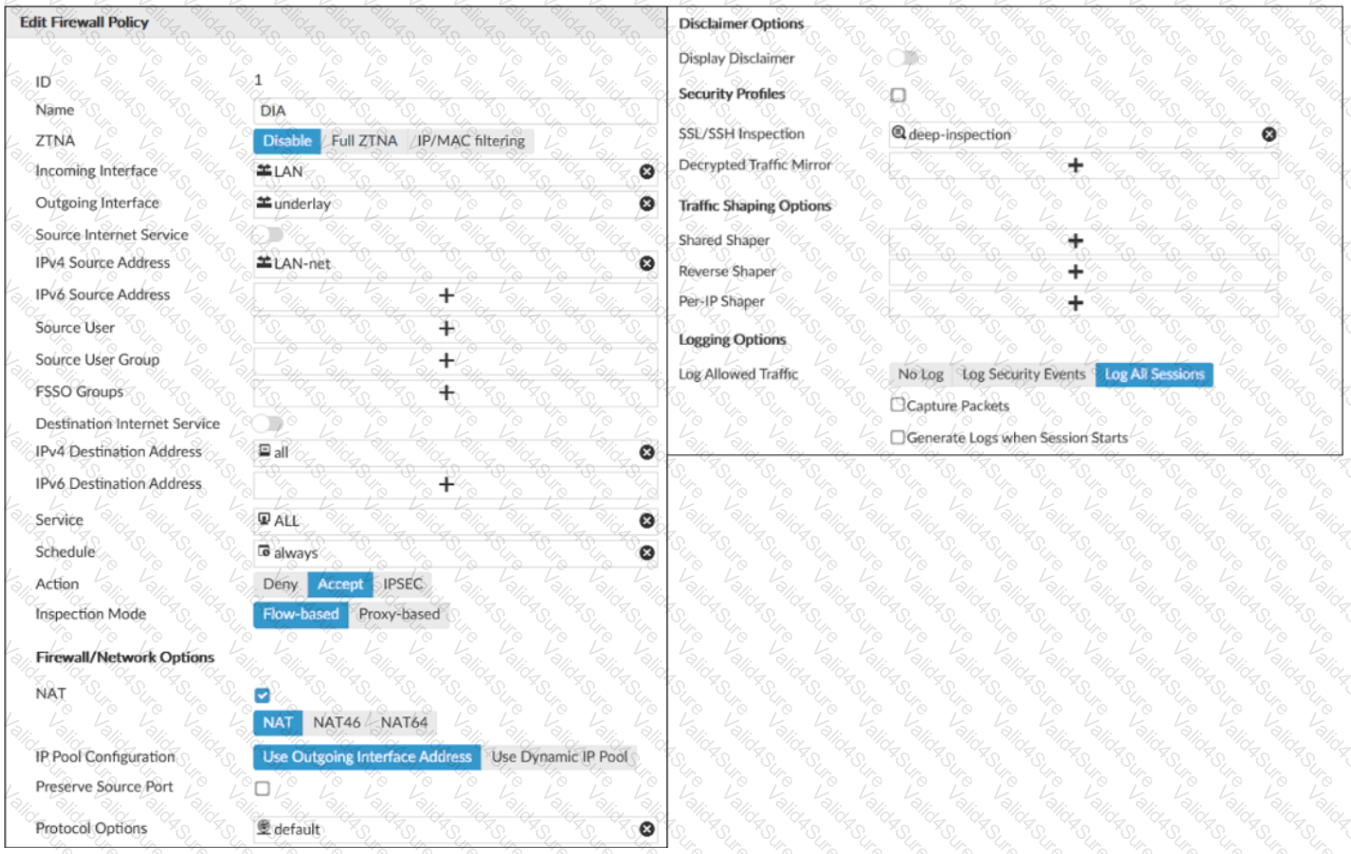
Exhibit A shows the traffic shaping policy and exhibit B shows the firewall policy.
The administrator wants FortiGate to limit the bandwidth used by YouTube. When testing, the administrator determines that FortiGate does not apply traffic shaping on YouTube traffic.
Based on the policies shown in the exhibits, what configuration change must be made so FortiGate performs traffic shaping on YouTube traffic?