NSE8_812 Exam Dumps - Network Security Expert 8 Written Exam
Searching for workable clues to ace the Fortinet NSE8_812 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s NSE8_812 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Refer to the exhibit, which shows the high availability configuration for the FortiAuthenticator (FAC1).
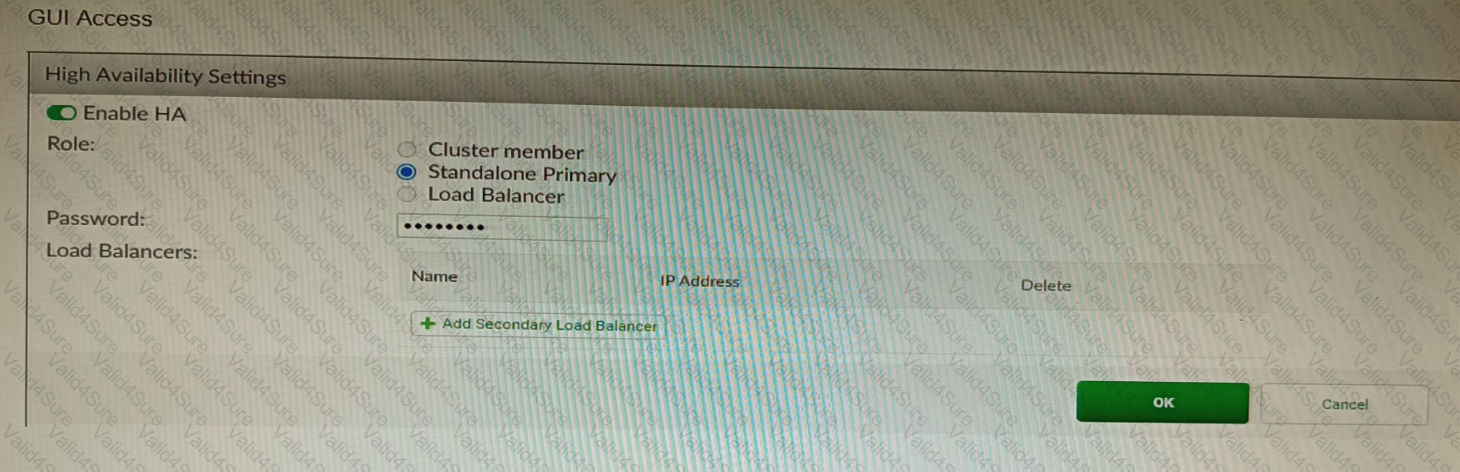
Based on this information, which statement is true about the next FortiAuthenticator (FAC2) member that will join an HA cluster with this FortiAuthenticator (FAC1)?
Refer to the exhibits.

During the implementation of a Fortinet Security Fabric configuration, CLI commands were issued in the order shown in the exhibit. On the next day, the local admin for FGTC issues the following command:
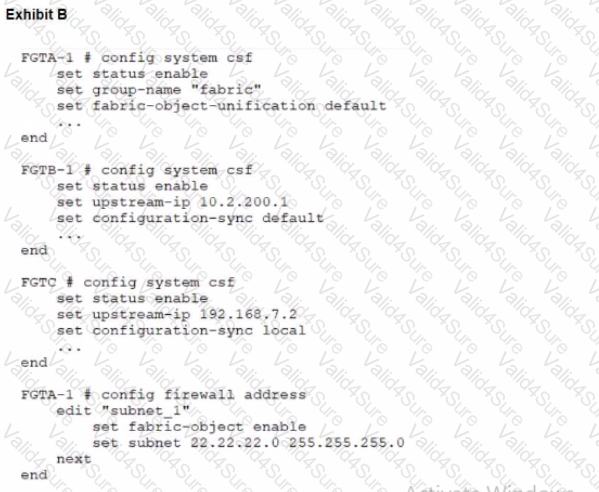
FGTC # config system csf
set configuration-sync default
end
In this scenario, which outcome is true regarding the "subnet_1" firewall address object on FGTC?
Refer to The exhibit, which shows a topology diagram.
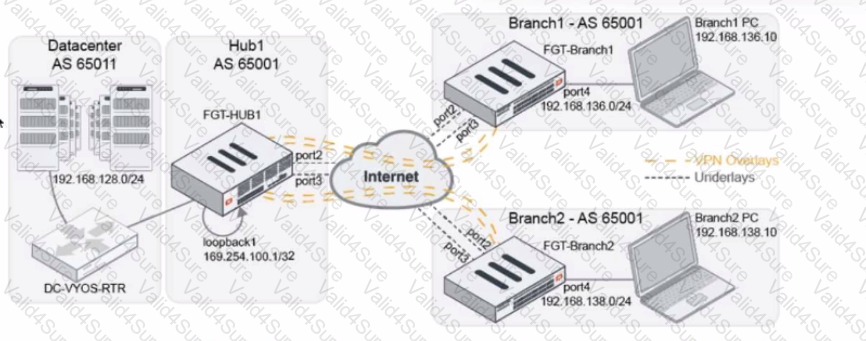
A customer wants to use SD-WAN for traffic generated from the data center towards Branches. SD-WAN on HUB should follow the underlay condition on each Branch and the solution should be scalable for hundreds of Branches.
Which SD WAN-Rules strategy should be used?
Refer to the exhibits.
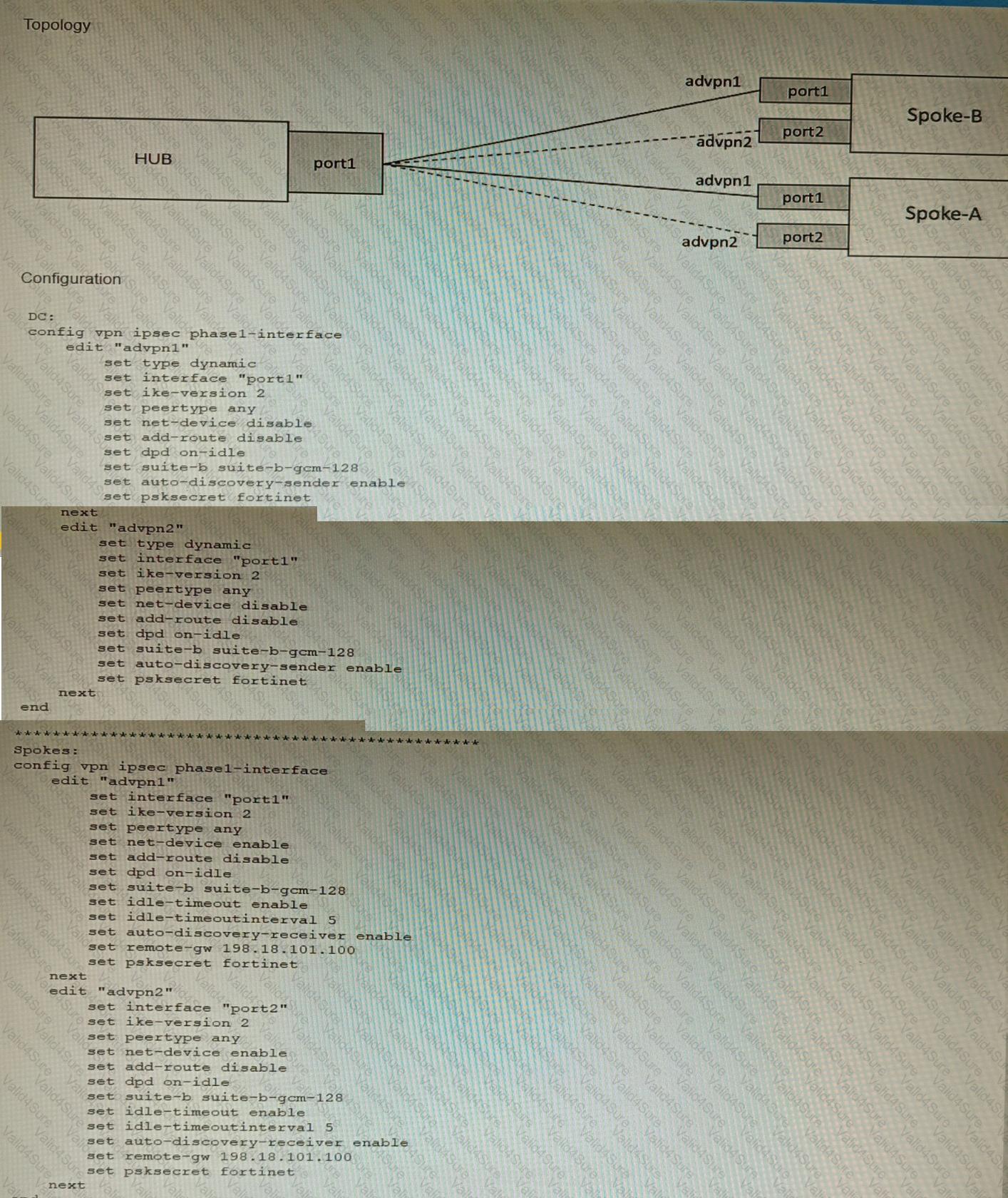
The exhibits show a diagram of a requested topology and the base IPsec configuration.
A customer asks you to configure ADVPN via two internet underlays. The requirement is that you use one interface with a single IP address on DC FortiGate.
In this scenario, which feature should be implemented to achieve this requirement?
Refer to the exhibit.
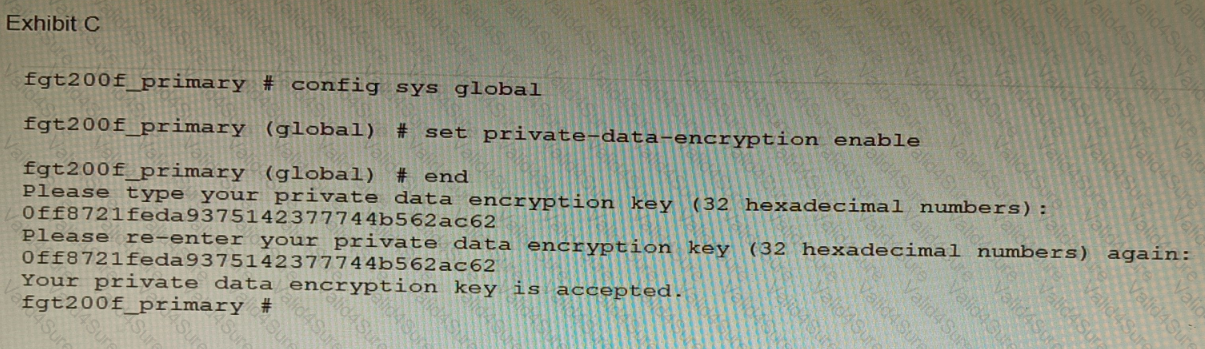
A customer has deployed a FortiGate 200F high-availability (HA) cluster that contains & TPM chip. The exhibit shows output from the FortiGate CLI session where the administrator enabled TPM.
Following these actions, the administrator immediately notices that both FortiGate high availability (HA) status and FortiManager status for the FortiGate are negatively impacted.
What are the two reasons for this behavior? (Choose two.)
A FortiGate running FortiOS 7.2.0 GA is configured in multi-vdom mode with a vdom set to vdom type Admin and another vdom set to vdom type Traffic.
Which two GUI sections are available on both VDOM types? (Choose two.)
A customer wants to use the FortiAuthenticator REST API to retrieve an SSO group called SalesGroup. The following API call is being made with the 'curl' utility:

Which two statements correctly describe the expected behavior of the FortiAuthenticator REST API? (Choose two.)
Refer to the exhibits.
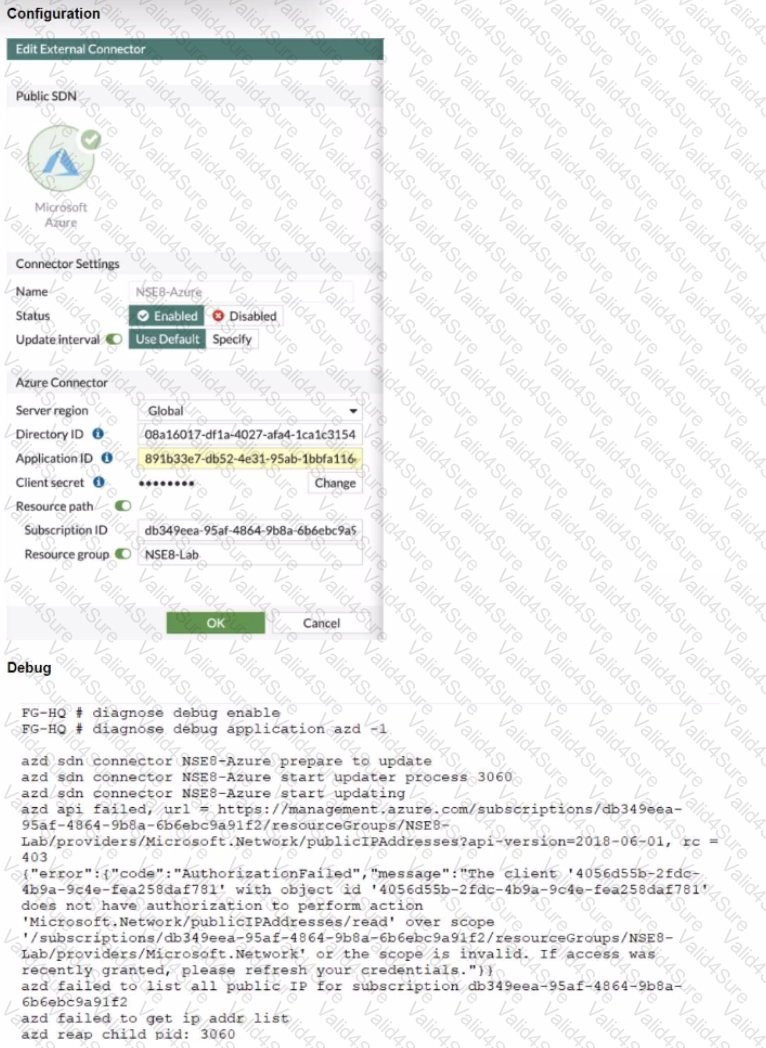
The exhibits show the configuration and debug output from a FortiGate Public SDN Connector.
What is a possible reason for this dynamic address object to be empty?