NSE8_812 Exam Dumps - Network Security Expert 8 Written Exam
An administrator has configured a FortiGate device to authenticate SSL VPN users using digital certificates. A FortiAuthenticator is the certificate authority (CA) and the Online Certificate Status Protocol (OCSP) server.
Part of the FortiGate configuration is shown below:
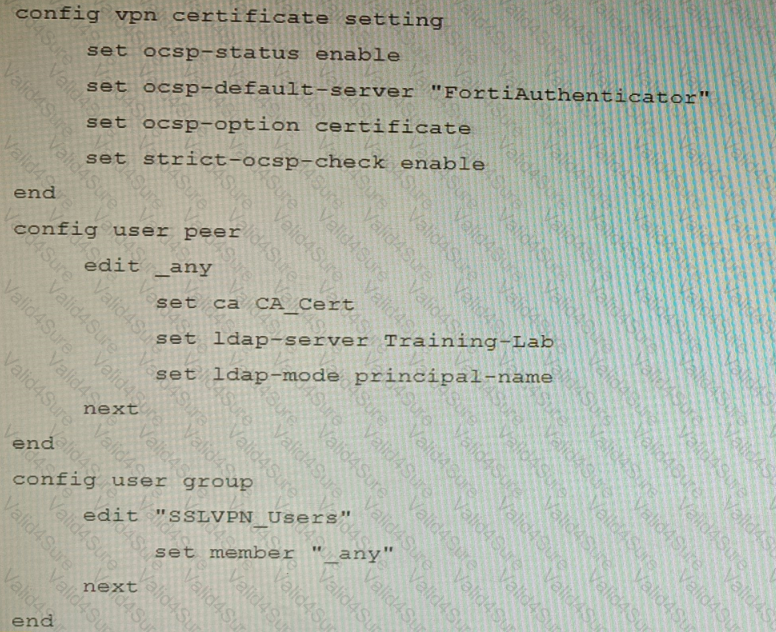
Based on this configuration, which two statements are true? (Choose two.)
Refer to the exhibit.
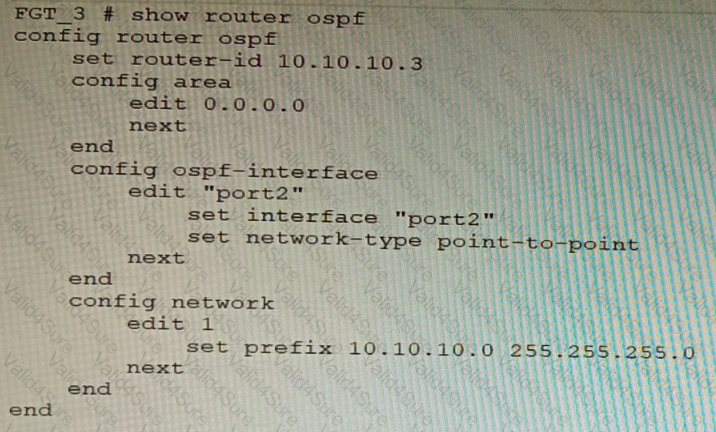
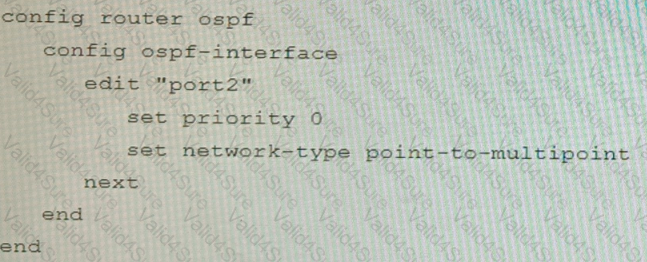
You are operating an internal network with multiple OSPF routers on the same LAN segment. FGT_3 needs to be added to the OSPF network and has the configuration shown in the exhibit. FGT_3 is not establishing any OSPF connection.
What needs to be changed to the configuration to make sure FGT_3 will establish OSPF neighbors without affecting the DR/BDR election?
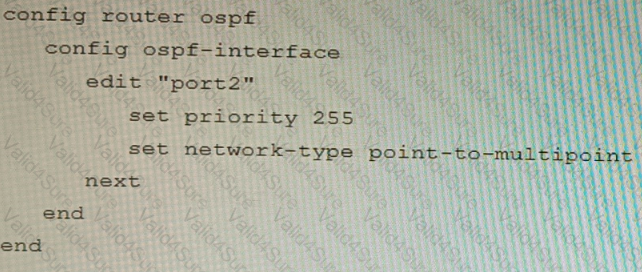
A)
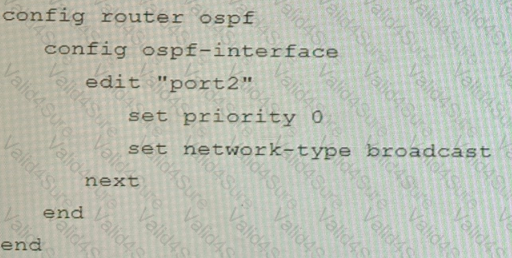
B)
C)
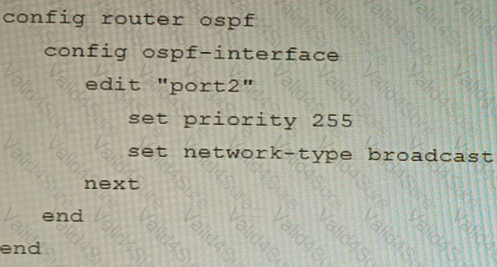
D)
Refer to the exhibits, which show a network topology and VPN configuration.
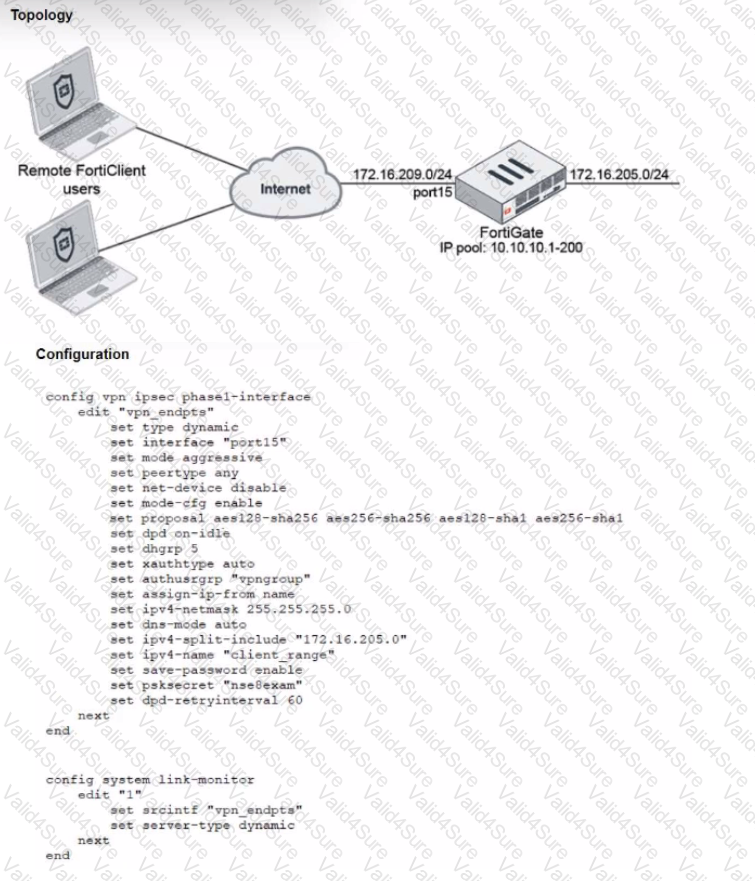
A network administrator has been tasked with modifying the existing dial-up IPsec VPN infrastructure to detect the path quality to the remote endpoints.
After applying the configuration shown in the configuration exhibit, the VPN clients can still connect and access the protected 172.16.205.0/24 network, but no SLA information shows up for the client tunnels when issuing the diagnose sys link-monitor tunnel all command on the FortiGate CLI.
What is wrong with the configuration?
Refer to the exhibit showing a firewall policy configuration.
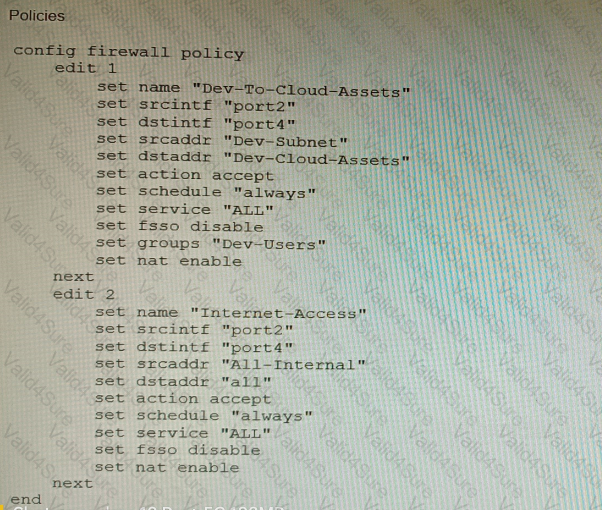
To prevent unauthorized access of their cloud assets, an administrator wants to enforce authentication on firewall policy ID 1.
What change does the administrator need to make?

You must analyze an event that happened at 20:37 UTC. One log relevant to the event is extracted from FortiGate logs:
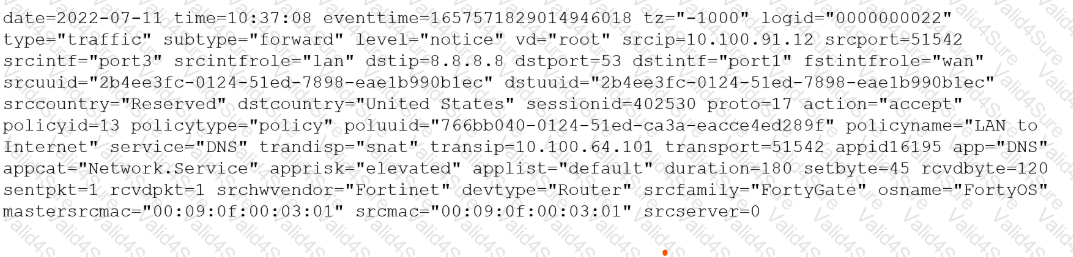
The devices and the administrator are all located in different time zones Daylight savings time (DST) is disabled
• The FortiGate is at GMT-1000.
• The FortiAnalyzer is at GMT-0800
• Your browser local time zone is at GMT-03.00
You want to review this log on FortiAnalyzer GUI, what time should you use as a filter?