NSK101 Exam Dumps - Netskope Certified Cloud Security Administrator (NCCSA)
Which two traffic steering configurations are supported by Netskope? (Choose two.)
You are asked to review files affected by malware in your organization. In this scenario, which two actions are possible and would be accessible from the Netskope UI -> Incidents --> Malware? (Choose two)
All users are going through Netskope's Next Gen SWG. Your CISO requests a monthly report of all users who are accessing cloud applications with a "Low" or a "Poor" CCL, where the activity is either "Edit" or "Upload".
Using the Advanced Analytics interface, which two statements describe which actions must be performed in this scenario? (Choose two.)
You want to deploy Netskope's zero trust network access (ZTNA) solution, NPA. In this scenario, which action would you perform to accomplish this task?
You added a new private app definition and created a Real-time Protection policy to allow access for all users. You have a user who reports that they are unable to access the application but all other applications work fine.
Which statement correctly describes how to troubleshoot this issue using the Netskope Web UI?
What are two fundamental differences between the inline and API implementation of the Netskope platform? (Choose two.)
You want to block access to sites that use self-signed certificates. Which statement is true in this scenario?
Click the Exhibit button.
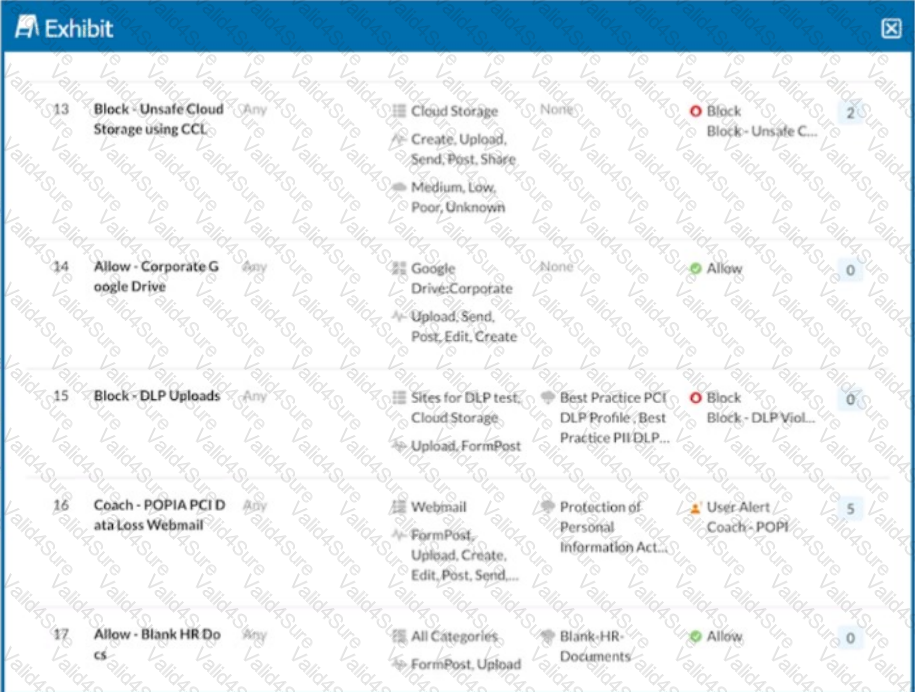
A user is uploading a file containing PCI-DSS data to the corporate Google Drive instance. You notice that the upload is not blocked by the policy shown in the exhibit. Which statement is correct in this scenario?