NSK101 Exam Dumps - Netskope Certified Cloud Security Administrator (NCCSA)
Exhibit
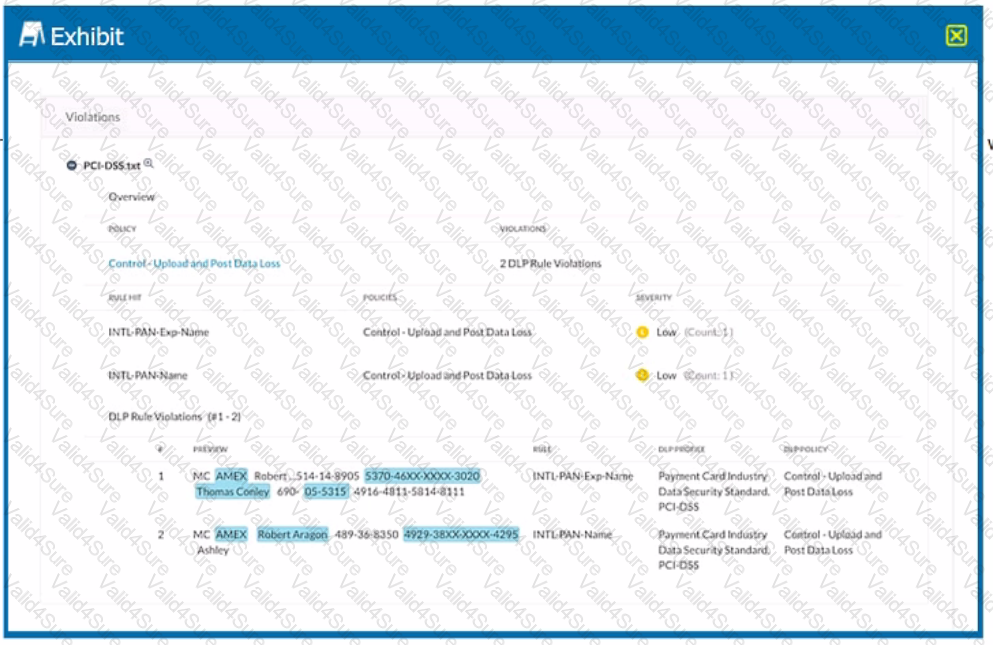
Which portion of the interface shown in the exhibit allows an administrator to set severity, assign ownership, track progress, and perform forensic analysis with excerpts of violating content?
An administrator wants to determine to which data plane a user is traversing. In this scenario, what are two ways to accomplish this task? (Choose two.)
Which two capabilities are part of Netskope's Adaptive Zero Trust Data Protection? (Choose two.)
Click the Exhibit button.
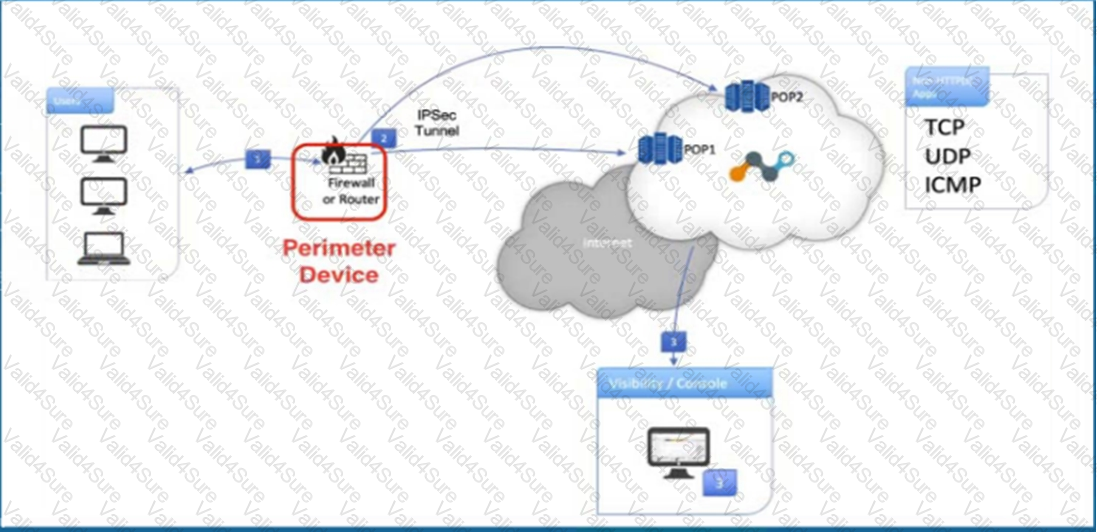
Referring to the exhibit, what are two recommended steps to be set on the perimeter device to monitor IPsec tunnels to a Netskope data plane? (Choose two.)
There is a DLP violation on a file in your sanctioned Google Drive instance. The file is in a deleted state. You need to locate information pertaining to this DLP violation using Netskope. In this scenario, which statement is correct?
What are two primary advantages of Netskope's Secure Access Service Edge (SASE) architecture? (Choose two.