PCNSE Exam Dumps - Palo Alto Networks Certified Security Engineer (PCNSE) PAN-OS 11.0
Which GloDalProtecI gateway setting is required to enable split-tunneting by access route, destination domain and application?
An engineer creates a set of rules in a Device Group (Panorama) to permit traffic to various services for a specific LDAP user group.
What needs to be configured to ensure Panorama can retrieve user and group information for use in these rules?
An engineer is monitoring an active/active high availability (HA) firewall pair.
Which HA firewall state describes the firewall that is currently processing traffic?
An engineer reviews high availability (HA) settings to understand a recent HA failover event Review the screenshot below.
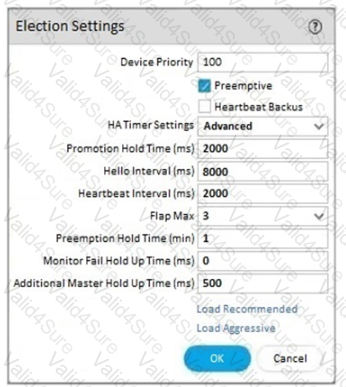
Which tuner determines how long the passive firewall will wart before taking over as the active firewall after losing communications with the HA peer?
Refer to Exhibit:
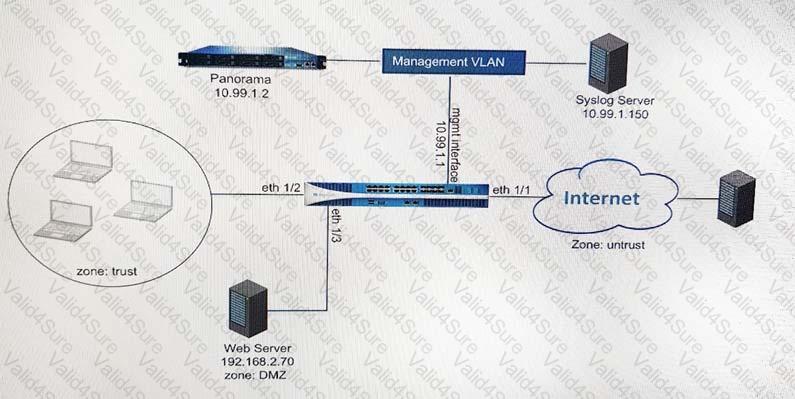
An administrator can not see any Traffic logs from the Palo Alto Networks NGFW in Panorama reports. The configuration problem seems to be on the firewall. Which settings, if configured incorrectly, most likely would stop only Traffic logs from being sent from the NGFW to Panorama?
A)
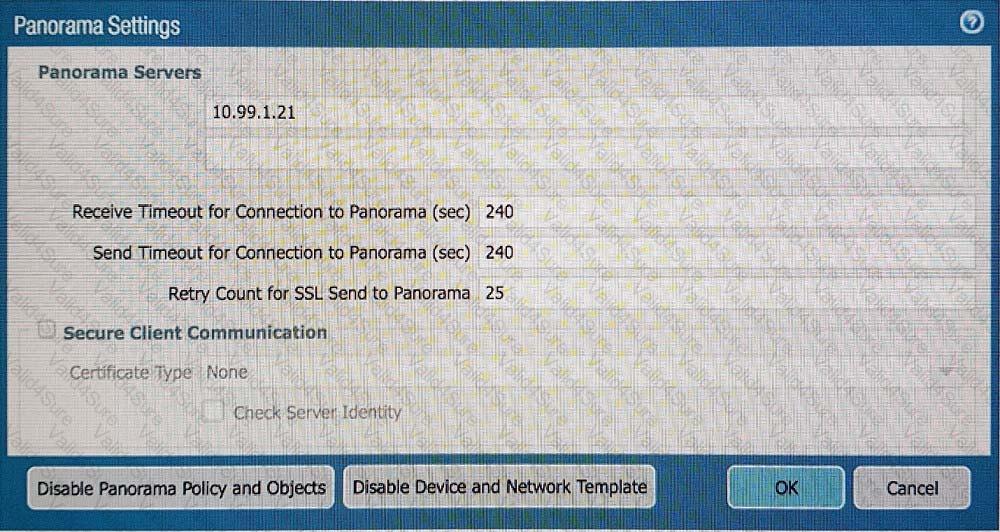
B)
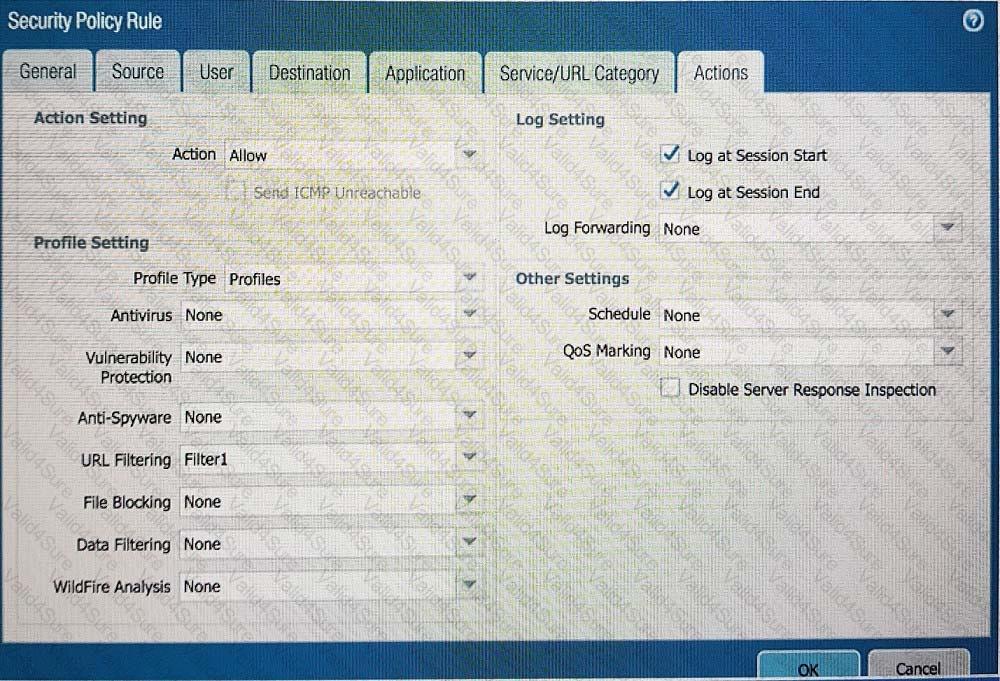
C)
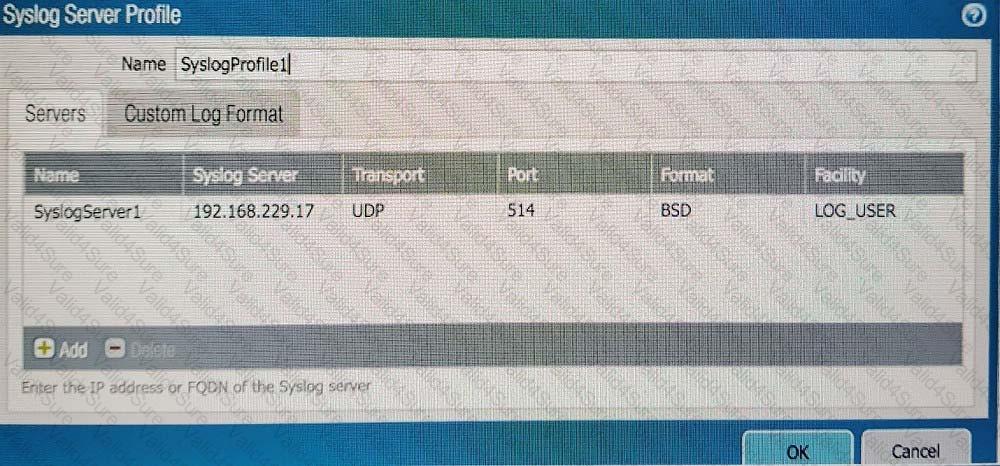
D)
An administrator has purchased WildFire subscriptions for 90 firewalls globally.
What should the administrator consider with regards to the WildFire infra-structure?
What does SSL decryption require to establish a firewall as a trusted third party and to establish trust between a client and server to secure an SSL/TLS connection'?
A network security administrator has been tasked with deploying User-ID in their organization.
What are three valid methods of collecting User-ID information in a network? (Choose three.)