PSE-Strata Exam Dumps - Palo Alto Networks System Engineer Professional - Strata
Searching for workable clues to ace the Paloalto Networks PSE-Strata Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s PSE-Strata PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
A customer is concerned about malicious activity occurring directly on their endpoints and will not be visible to their firewalls.
Which three actions does the Traps agent execute during a security event, beyond ensuring the prevention of this activity? (Choose three.)
What are two benefits of using Panorama for a customer who is deploying virtual firewalls to secure data center traffic? (Choose two.)
Which are the three mandatory components needed to run Cortex XDR? (Choose three.)
What are two ways to manually add and remove members of dynamic user groups (DUGs)? (Choose two)
Which of the following statements is valid with regard to Domain Name System (DNS) sinkholing?
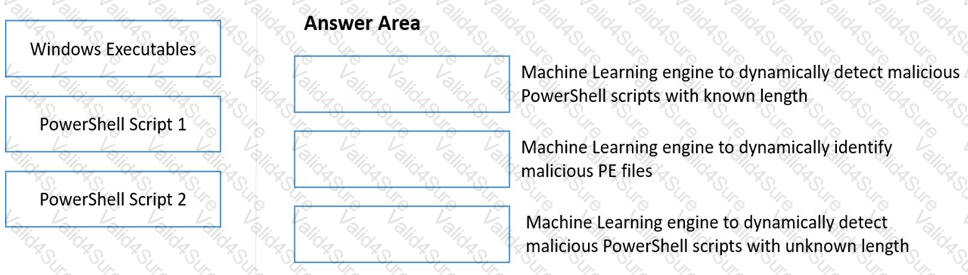
Match the WildFire Inline Machine Learning Model to the correct description for that model.
In which two ways can PAN-OS software consume MineMeld outputs? (Choose two.)