SC-200 Exam Dumps - Microsoft Security Operations Analyst
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have Linux virtual machines on Amazon Web Services (AWS).
You deploy Azure Defender and enable auto-provisioning.
You need to monitor the virtual machines by using Azure Defender.
Solution: You manually install the Log Analytics agent on the virtual machines.
Does this meet the goal?
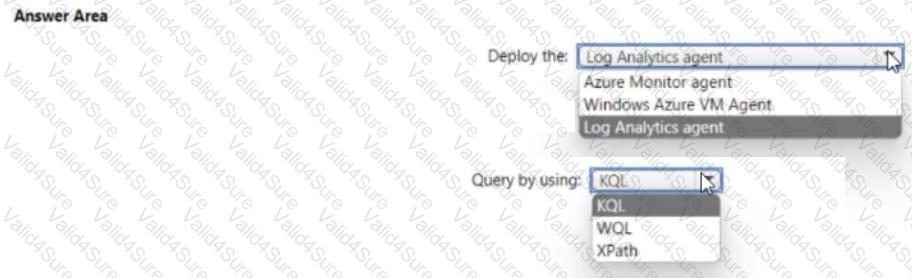
You need to meet the Microsoft Sentinel requirements for collecting Windows Security event logs. What should you do? To answer, select the appropriate options in the answer area. NOTE Each correct selection is worth one point.
You have an Azure subscription that uses Microsoft Defender for Cloud.
You have a GitHub account named Account1 that contains 10 repositories.
You need to ensure that Defender for Cloud can assess the repositories in Account1.
What should you do first in the Microsoft Defender for Cloud portal?
You have an Azure subscription that uses Microsoft Defender XDR.
From the Microsoft Defender portal, you perform an audit search and export the results as a file named Filel.csv that contains 10,000 rows.
You use Microsoft Excel to perform Get & Transform Data operations to parse the AuditData column from Filel.csv. The operations fail to generate columns for specific JSON properties.
You need to ensure that Excel generates columns for the specific JSON properties in the audit search results.
Solution: From Excel, you apply filters to the existing columns in Filel.csv to reduce the number of rows, and then you perform the Get & Transform Data operations to parse the AuditData column.
Does this meet the requirement?
You have a Microsoft 365 subscription that uses Microsoft Defender for Endpoint Plan 2 and contains a Windows device named Device!.
You initiated a live response session on Device1.
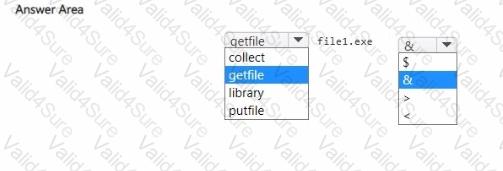
You need to run a command that will download a 250-MB file named File! .exe from the live response library to Device1. The solution must ensure that Filel.exe is downloaded as a background process.
How should you complete the live response command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription that uses Microsoft Defender XDR.
You are investigating an attacker that is known to use the Microsoft Graph API as an attack vector. The attacker performs the tactics shown the following table.

You need to search for malicious activities in your organization.
Which tactics can you analyze by using the MicrosoftGraphActivityLogs table?
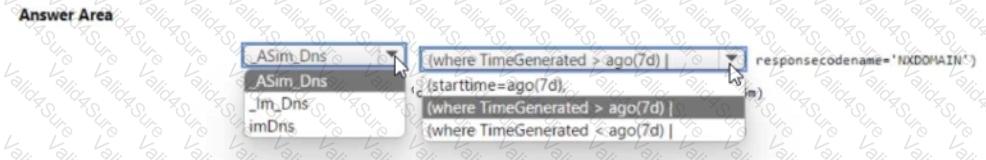
You need to create a query to investigate DNS-related activity. The solution must meet the Microsoft Sentinel requirements. How should you complete the Query? To answer, select the appropriate options in the answer area NOTE: Each correct selection is worth one point.
You have an Azure subscription that uses Microsoft Defender for Cloud.
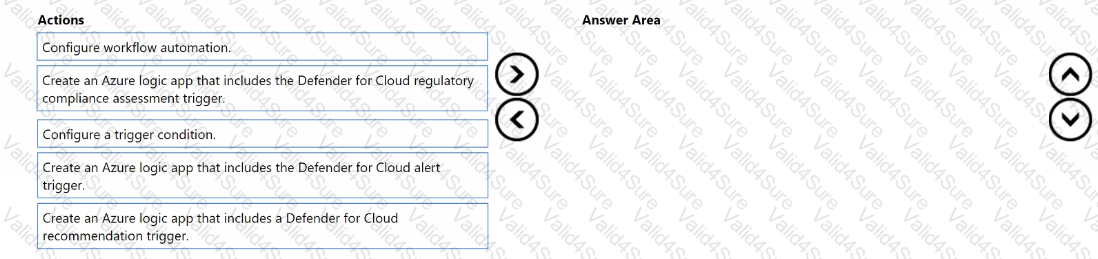
You need to create a workflow that will send a Microsoft Teams message to the IT department of your company when a new Microsoft Secure Score action is generated.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.