SC-200 Exam Dumps - Microsoft Security Operations Analyst
Searching for workable clues to ace the Microsoft SC-200 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s SC-200 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint.
You have the on-premises devices shown in the following table.
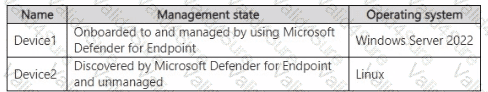
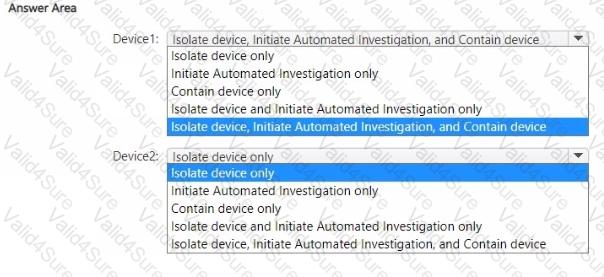
You are preparing an incident response plan for devices infected by malware. You need to recommend response actions that meet the following requirements:
• Block malware from communicating with and infecting managed devices.
• Do NOT affect the ability to control managed devices.
Which actions should you use for each device? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You need to restrict cloud apps running on CLIENT1 to meet the Microsoft Defender for Endpoint requirements.
Which two configurations should you modify? Each correct answer present part of the solution.
NOTE: Each correct selection is worth one point.
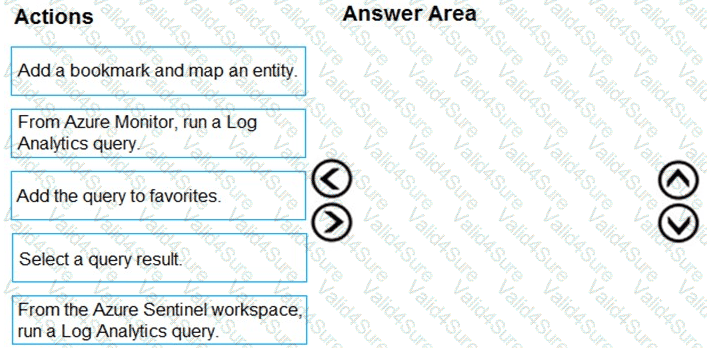
You need to add notes to the events to meet the Azure Sentinel requirements.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of action to the answer area and arrange them in the correct order.
Which rule setting should you configure to meet the Microsoft Sentinel requirements?
You need to configure the Microsoft Sentinel integration to meet the Microsoft Sentinel requirements. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.

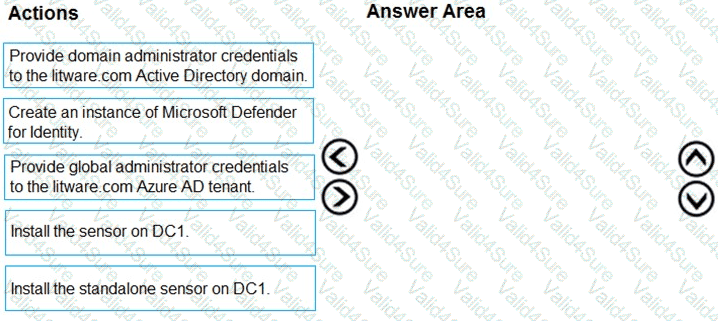
You need to configure DC1 to meet the business requirements.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You need to assign a role-based access control (RBAC) role to admin1 to meet the Azure Sentinel requirements and the business requirements.
Which role should you assign?
You need to modify the anomaly detection policy settings to meet the Cloud App Security requirements. Which policy should you modify?



