SC-300 Exam Dumps - Microsoft Identity and Access Administrator
Searching for workable clues to ace the Microsoft SC-300 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s SC-300 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
You need to track application access assignments by using Identity Governance. The solution must meet the delegation requirements.
What should you do first?
You have an Azure Active Directory (Azure AD) tenant named contoso.com.
All users who run applications registered in Azure AD are subject to conditional access policies.
You need to prevent the users from using legacy authentication.
What should you include in the conditional access policies to filter out legacy authentication attempts?
You have a Microsoft 365 tenant.
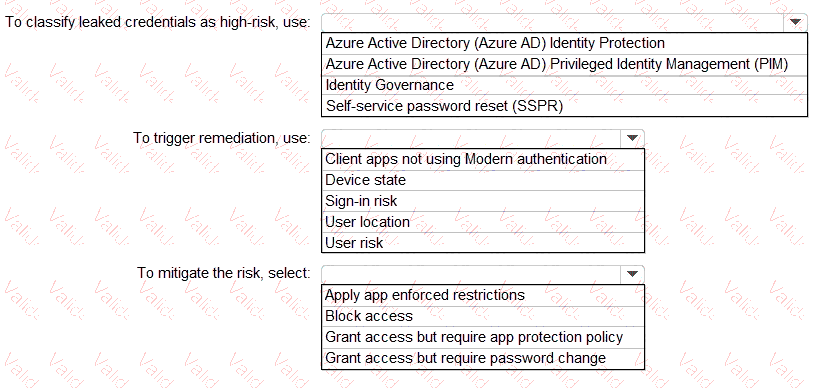
You need to identify users who have leaked credentials. The solution must meet the following requirements.
• Identity sign-Ins by users who ate suspected of having leaked credentials.
• Rag the sign-ins as a high risk event.
• Immediately enforce a control to mitigate the risk, while still allowing the user to access applications.
What should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
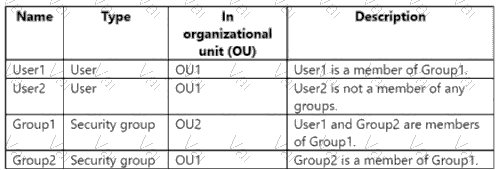
Your network contains an on-premises Active Directory domain named contoso.com. The domain contains the objects shown in the following table.
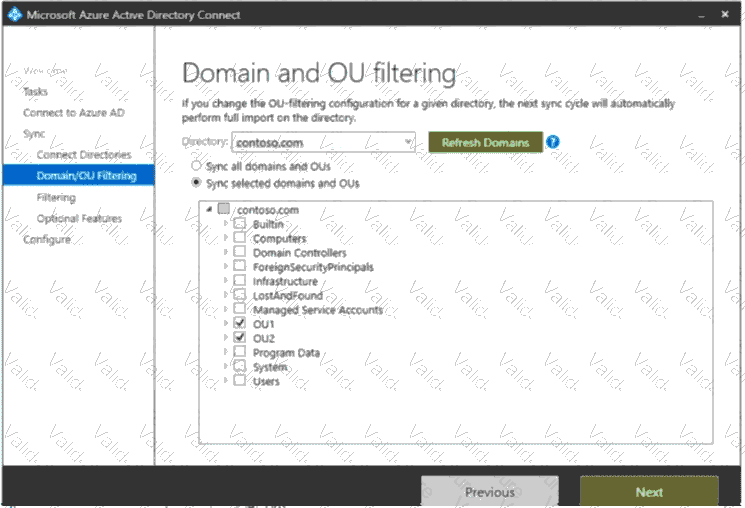
You install Microsoft Entra Connect. You configure the Domain and OU filtering settings as shown in the Domain and OU Filtering exhibit. (Click the Domain and OU Filtering tab.)
You configure the Filter users and devices settings as shown in the Filter Users and Devices exhibit. (Click the Filter Users and Devices tab.)
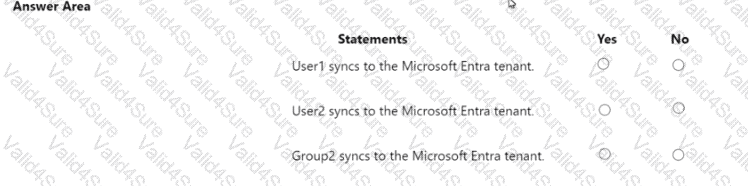
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
You need to be able to create a Microsoft Defender for Cloud Apps session policy.
What should you do first?
You have an Azure subscription named Sub1 that contains two resource groups named RG1 and RG2. Sub1 contains the users shown in the following table.
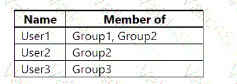
Sub1 contains the resources shown in the following table.
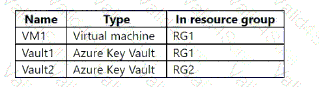
You create the role-based access control (RBAC) role assignments shown in the following table.
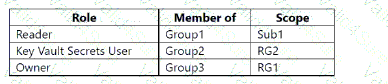
For each of the following statements, select Yes if the statement is true. Otherwise, select No NOTE: Each correct selection is worth one point.

Your company has an Azure Active Directory (Azure AD) tenant named contosri.com. The company has the business partners shown in the following table.

users can request access by using package 1.
Users at Fabrikam and Litware use ail then respective domain names for email addresses.
You plan to create an access package named packaqe1 that will be accessible only to the Fabrikam and Litware users.
You need to configure connected organizations for Fabrikam and litware so that any of their users can request access by using package1.
What is the minimum of connected organization that you should create.
You have accounts for the following cloud platforms:
• Azure
• Alibaba Cloud
• Amazon Web Services (AWS)
• Google Cloud Platform (GCP)
You configure an A2ure subscription to use Microsoft Entra Permissions Management to manage the permissions in Azure only. Which additional cloud platforms can be managed by using Permissions Management?
