SC-300 Exam Dumps - Microsoft Identity and Access Administrator
Searching for workable clues to ace the Microsoft SC-300 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s SC-300 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Task 6
You need to implement additional security checks before the members of the Sg-Executive can access any company apps. The members must meet one of the following conditions:
• Connect by using a device that is marked as compliant by Microsoft Intune.
• Connect by using client apps that are protected by app protection policies.
Task 3
You need to add the Linkedln application as a resource to the Sales and Marketing access package. The solution must NOT remove any other resources from the access package.
You have three Azure subscriptions that are linked to a single Microsoft Entra tenant.
You need to evaluate and remediate the risks associated with highly privileged accounts. The solution must minimize administrative effort.
What should you use?
You need to resolve the issue of the guest user invitations. What should you do for the Azure AD tenant?
You need to implement the planned changes for litware.com. What should you configure?
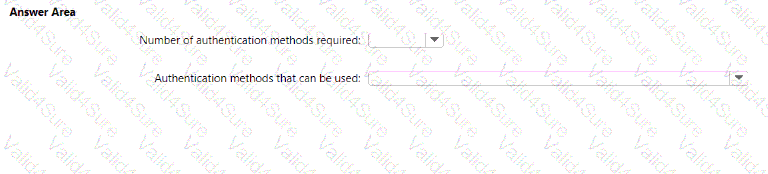
You implement the planned changes for SSPR.
What occurs when User3 attempts to use SSPR? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription that uses Microsoft Defender for Cloud Apps.
You have multiple third-party apps that access the resources in the subscription.
You need to monitor the access of the third-party apps.
What should you create?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You use Azure Monitor to analyze Azure Active Directory (Azure AD) activity logs.
You receive more than 100 email alerts each day for failed Azure AD user sign-in attempts.
You need to ensure that a new security administrator receives the alerts instead of you.
Solution: From Azure AD, you modify the Diagnostics settings.
Does this meet the goal?
